/ Was ist das Purdue-Modell für ICS-Sicherheit?
Was ist das Purdue-Modell für ICS-Sicherheit?
Welchen Zweck erfüllt das Purdue-Modell?
Das Purdue-Modell wurde im Rahmen der Purdue Enterprise Reference Architecture (PERA) als Referenzmodell für Datenflüsse in der computerintegrierten Fertigung (CIM) entwickelt, bei der die Prozesse einer Fabrik vollständig automatisiert sind. Es definierte den Standard für den Aufbau einer ICS-Netzwerkarchitektur, die die OT-Sicherheit unterstützt, indem die Netzwerkebenen getrennt werden, um einen hierarchischen Datenfluss zwischen ihnen aufrechtzuerhalten.
Das Modell zeigt, wie die typischen Elemente einer ICS-Architektur miteinander verbunden sind, und gliedert sie in sechs Zonen, die Informationstechnologie- (IT) und OT-Systeme enthalten. Bei richtiger Umsetzung unterstützt es die Einrichtung eines Air-Gaps zwischen ICS/OT- und IT-Systemen und isoliert sie, damit das Unternehmen wirksame Zugriffskontrollen durchsetzen kann, ohne den Geschäftsbetrieb zu behindern.
Zonen des Purdue-Modells
OT-Systeme belegen die unteren Ebenen des Modells, während IT-Systeme die oberen Ebenen belegen. Beide Bereiche werden durch eine dazwischenliegende Konvergenzzone voneinander getrennt.
Schauen wir uns die einzelnen Zonen im Purdue-Referenzmodell von oben nach unten an:
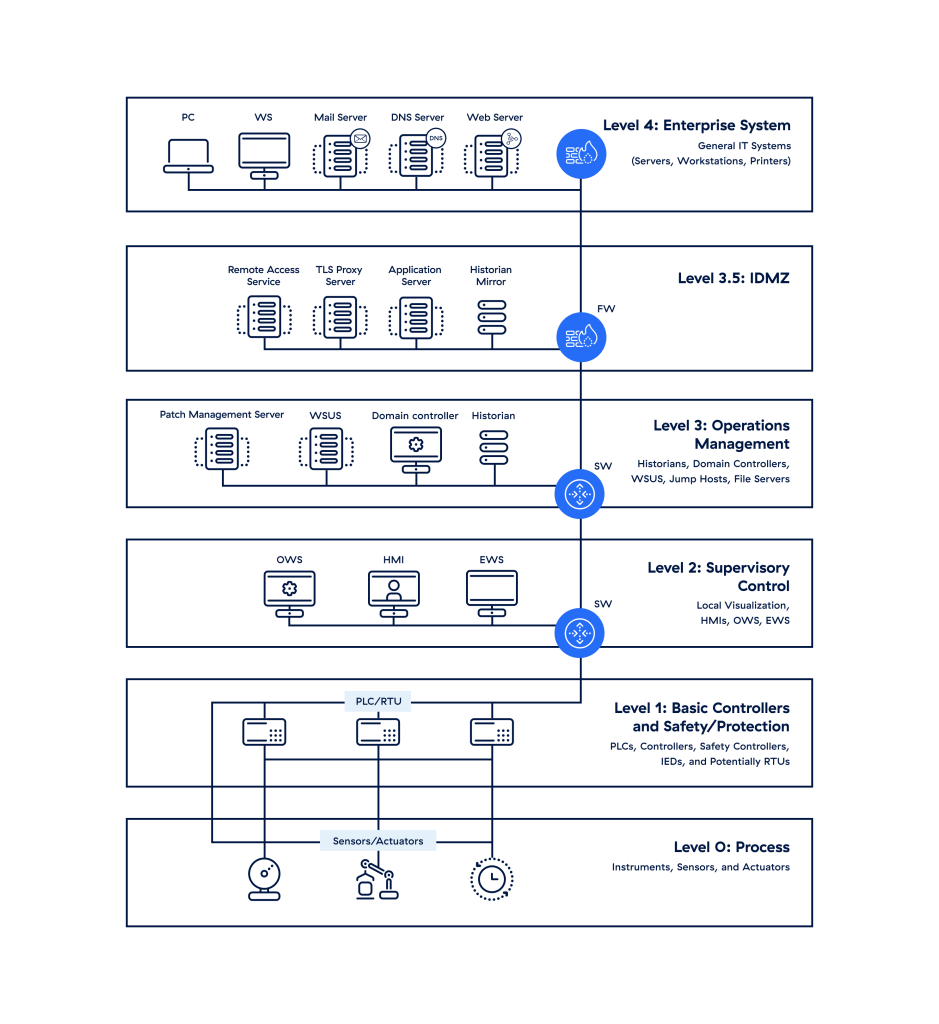
Abb. 1:Einfaches Rendering des Purdue-Modells
Ebene 4/5: Zone für Geschäftsanwendungen
In diesen Zonen befindet sich das typische IT-Netzwerk, in dem die wichtigsten Geschäftsfunktionen stattfinden, einschließlich der Orchestrierung der Fertigungsabläufe. Enterprise-Resource-Planning-Systeme (ERP) steuern hier die Produktionspläne, den Materialverbrauch, den Versand und die Lagerbestände der Anlagen.
Störungen auf dieser Ebene können zu längeren Ausfallzeiten führen und so wirtschaftliche Schäden, Ausfälle kritischer Infrastrukturen oder Umsatzeinbußen verursachen.
Ebene 3.5: Konvergenzzone/Demilitarized Zone (DMZ)
Diese Zone umfasst Sicherheitssysteme wie Firewalls und Proxys, die verwendet werden, um die laterale Ausbreitung von Bedrohungen zwischen IT und OT zu verhindern. Mit der zunehmenden Automatisierung ist der Bedarf an bidirektionalen Datenflüssen zwischen OT- und IT-Systemen gestiegen. Diese IT-OT-Konvergenzschicht kann Unternehmen einen Wettbewerbsvorteil verschaffen. Allerdings kann sie auch ihr Cyberrisiko erhöhen, wenn sie einen flachen Netzwerkansatz verfolgen.
Ebene 3: Zone für Fertigungsbetriebssysteme
Diese Zone enthält unternehmensspezifische OT-Geräte, die die Produktionsabläufe in der Fabrikhalle verwalten:
- MOM-Systeme (Manufacturing Operations Management) verwalten Produktionsabläufe.
- MES-Systeme (Manufacturing Execution) erfassen Echtzeitdaten, um die Produktion zu optimieren.
- Datenhistoriker speichern Prozessdaten und führen (in heutigen Lösungen) Kontextanalysen durch.
Wie bei den Ebenen 4 und 5 können Störungen auf dieser Ebene zu wirtschaftlichen Schäden, zum Ausfall kritischer Infrastrukturen, zur Gefährdung der Sicherheit von Menschen und Anlagen oder zu Umsatzeinbußen führen.
Ebene 2: Steuerungssystemzone
Diese Zone enthält Systeme, die physische Prozesse überwachen, kontrollieren und steuern:
- Mithilfe von SCADA-Software (Supervisory Control and Data Acquisition) werden physische Prozesse lokal oder per Remotezugriff überwacht und gesteuert und Daten aggregiert, um sie an Datenhistoriker zu senden.
- Distributed Control Systems (DCS) führen SCADA-Funktionen aus, werden jedoch normalerweise lokal bereitgestellt.
- Mensch-Maschine-Schnittstellen (HMIs) stellen eine Verbindung zu DCS und SPS her, um grundlegende Steuerungs- und Überwachungsfunktionen zu ermöglichen.
Ebene 1: Zone für intelligente Geräte
Diese Zone enthält Instrumente, die Befehle an die Geräte auf Ebene 0 senden:
- Programmable Logic Controllers (PLCs) überwachen automatisierte oder menschliche Eingaben in industriellen Prozessen und nehmen entsprechende Ausgabeanpassungen vor.
- Remote Terminal Units (RTUs) verbinden Hardware auf Ebene 0 mit Systemen auf Ebene 2.
Ebene 0: Zone für physische Prozesse
Diese Zone enthält Sensoren, Aktoren und andere Maschinen, die direkt für die Montage, das Schmieren und andere physische Prozesse verantwortlich sind. Viele heutige Sensoren kommunizieren über Mobilfunknetze direkt mit Überwachungssoftware in der Cloud.
Abbildung 2 zeigt den Arbeitsablauf und die Interaktionen zwischen den verschiedenen Zonen und Systemen.
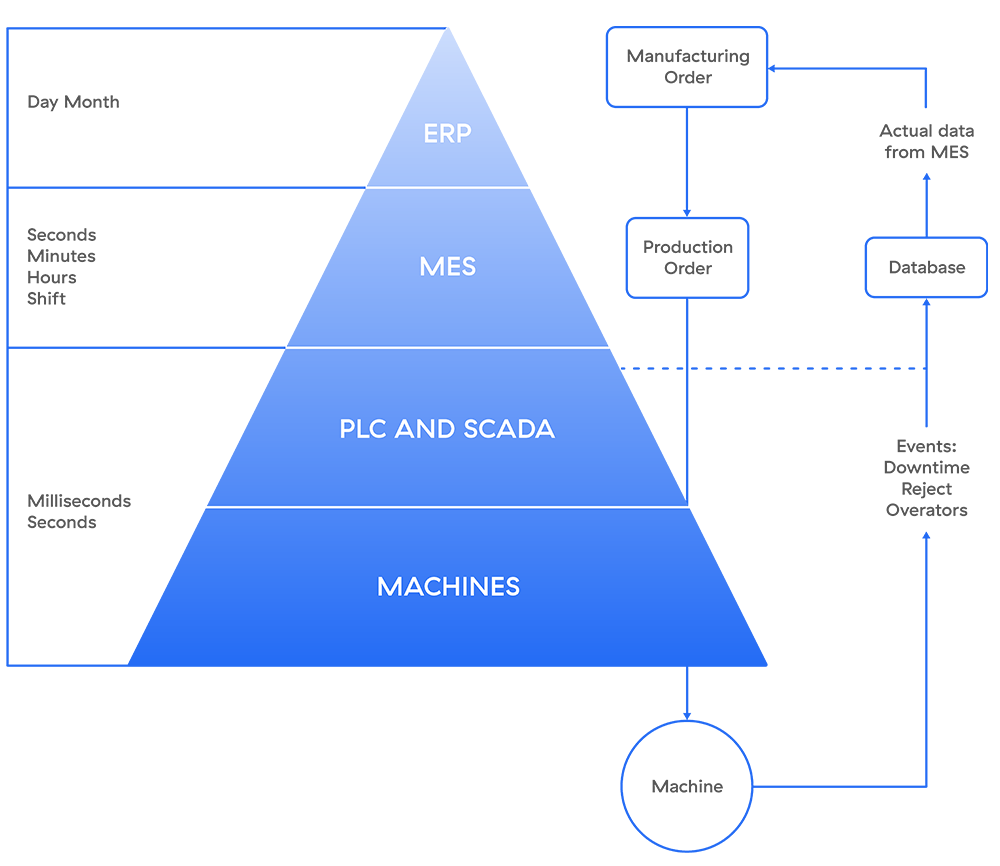
Abb. 2:Arbeitsablauf und Interaktionen im Purdue-Modell
Ist das Purdue-Modell noch relevant?
CIM begann sich Mitte bis Ende der 1980er Jahre in der Branche durchzusetzen. Das Purdue-Modell wurde 1992 von Theodore J. Williams und dem Purdue University Consortium als eines der ersten vorgestellt, die eine klare Informationshierarchie skizzierten.
Da das industrielle Internet der Dinge (IIoT) die Grenzen zwischen IT und OT zunehmend verwischt, steht die Frage im Raum, inwieweit das Purdue-Modell noch auf heutige ICS-Netzwerke anwendbar ist. Im Zuge der Direktübertragung von Daten von Ebene 0 in die Cloud wird das Segmentierungsframework des Purdue-Modells häufig außer Kraft gesetzt. Viele halten es trotzdem für verfrüht, das Modell zu verwerfen.
So meinte Vatsal Shah, CEO von Litmus, im Jahr 2020: „Das Purdue-Modell erfüllt weiterhin die Segmentierungsanforderungen sowohl für drahtlose als auch für kabelgebundene Netzwerke und schützt OT-Netzwerke vor unerwünschtem Traffic und Exploits.“¹
Das SANS Institute vertrat 2021 eine ähnliche Position und erklärte: „Obwohl die hierarchischen Ebenen nicht mehr auf alle heutigen Architekturen angewendet werden können, hilft die Sortierung von ICS- und IT-Geräten und -Systemen in unterschiedliche Funktionsebenen Administratoren und Sicherheitsexperten dabei, zu bestimmen, wo Sicherheitsmaßnahmen effektiv angewendet werden können.“²
Ähnlich konstatierte Forbes 2022: „Das Purdue-Modell ist tot. Lang lebe das Purdue-Modell.“³
Aufgrund der speziellen Betriebszeitanforderungen und Budgets, die im industriellen Bereich gelten, ist es oft nicht möglich, alte Systeme und Lösungen durch neue zu ersetzen. Trotz der zunehmenden Bedeutung des IoT gilt das auch für das Purdue-Modell. Stattdessen plädieren viele Experten für einen hybriden Ansatz, bei dem Makrosegmentierung mit Zero Trust angewendet wird, um die einzigartigen Herausforderungen zukunftsfähiger ICS-Sicherheit zu bewältigen.
1. AutomationWorld, „Is the Purdue Model Still Relevant?“ Mai 2020.
2. SANS Institute, „Introduction to ICS Security Part 2“, Juli 2021.
3. Forbes, „A Reimagined Purdue Model For Industrial Security Is Possible“, Januar 2022.
Cybersicherheitsherausforderungen speziell für ICS
Schauen wir uns einige dieser Herausforderungen genauer an:
- Air-Gaps funktionieren nicht mehr. Die zunehmende Nutzung von IoT und Cloud in industriellen Wertschöpfungsketten hat dazu geführt, dass viele industrielle Netzwerke so stark integriert sind, dass herkömmliche Air-Gaps ihre Wirksamkeit verloren haben.
- ICS-Geräte wurden für eine lange Lebensdauer und nicht für laufende Weiterentwicklung entwickelt. Aufgrund der strengen Anforderungen an die Betriebszeit vieler Industriegeräte ist es schwierig, kostspielig oder riskant, sie zu aktualisieren oder zu ersetzen. Daher bleiben viele CIM-Geräte mit dem größeren Netzwerk verbunden, obwohl sie anfällig für neuartige Angriffe sind.
- IT-OT-Konvergenz und neue Technologien erhöhen das Risiko. Während herkömmliche Barrieren zwischen IT und OT im Zuge der digitalen Transformation aufgehoben werden, Fortschritte in der Vernetzung und Datenanalyse Prozesse umgestalten und neue, raffinierte Cyberangriffe auftauchen, passen sich ICS-Frameworks nur langsam an.
- Viele ICS-Netzwerkverantwortliche zögern bei der Umstellung auf Zero Trust. Bedenken in Bezug auf Ausfallzeiten, die zu Umsatzeinbußen, Störungen der Infrastruktur oder sogar einer Gefährdung der Sicherheit von Menschen führen können, verunsichern Industriebetreiber hinsichtlich möglicher Kompromisse bei Kosten und Komplexität. Dennoch ist und bleibt Zero Trust die effektivste Strategie zur Sicherung zukunftsfähiger Netzwerke.
Die Notwendigkeit von Zero Trust in ICS
In OT-Umgebungen kommen häufig flache Netzwerke und Geräte mehrerer Anbieter zum Einsatz. Allerdings kann die Mikrosegmentierung auf Netzwerkebene mit physischen Geräten erhebliche Ausfallzeiten bedeuten – insbesondere, wenn die ICS- und SCADA-Systeme zu veraltet sind. Darüber hinaus kennen sich die meisten OT-Experten weder mit den Best Practices der IT noch mit fortgeschrittenen Konzepten der Netzwerksicherheit aus. Ihre Aufgabe besteht darin, der Betriebszeit und dem Mitarbeiterschutz Priorität einzuräumen, nicht der Sicherheit.
Ethernet ist noch immer das Rückgrat der meisten Fabriken und Lagerhallen. Drahtlose Konnektivität gewinnt jedoch an Bedeutung, da private Mobilfunknetze Mobilität, Zuverlässigkeit, deterministische Vernetzung und standardisierte Technologie bieten. Dies ermöglicht den Einsatz von Industrie-4.0-Anwendungen wie autonomen mobilen Robotern, Cobots, Asset Tracking und Smart Glasses.
Heute können Hersteller Daten in Echtzeit erfassen und diese nutzen, um Analysen in der Cloud durchzuführen und sofort Ergebnisse zu erzielen. Auch Anwendungen und datengenerierende Aktivitäten, die früher lokalen Vorgängen vorbehalten waren – SPS, SCADA und DCS für die Fertigung sowie Lagerverwaltungssysteme für die Logistik –, werden in die Cloud verlagert und erhöhen so die Komplexität des OT-Netzwerks.
Zero Trust kann die Sicherheit für OT-Umgebungen vereinfachen und kritische Herausforderungen wie den sicheren Remotezugriff auf ICS-Systeme lösen, ohne dass auf jeder Ebene eine physische Segmentierung erforderlich ist. Das National Institute of Standards and Technology (NIST) empfiehlt die Zero-Trust-Architektur für Industrie- und Unternehmensnetzwerke. Dazu heißt es: „Auch die perimeterbasierte Netzwerksicherheit hat sich als unzureichend erwiesen, da Angreifer, sobald sie den Perimeter durchbrechen, ungehindert weiter lateral vordringen können.“
Die Anwendung der Zero-Trust-Leitprinzipien von IT-Netzwerken für Arbeitsabläufe, Systemdesign und Betrieb kann den Sicherheitsstatus von OT-Netzwerken vereinfachen und verbessern und zur Beschleunigung der digitalen Transformation beitragen.
Die ICS-Sicherheitslösung von Zscaler
Ein Zero-Trust-Ansatz ist der effektivste Weg, um robuste OT- und ICS-Sicherheit zu gewährleisten, mit adaptivem, kontextbasiertem Anwendungszugriff, der nicht vom Netzwerkzugriff abhängt. Mit einer effektiven Zero-Trust-Architektur kann jeder User nur auf die Anwendungen und Systeme zugreifen, die er benötigt, ohne dass komplexe Firewall-Stacks oder VPNs erforderlich sind. Ihre Anwendungen und Ihr Netzwerk werden dabei nicht im Internet exponiert.
Zscaler Private Access™ (ZPA™) ist die weltweit am häufigsten eingesetzte ZTNA-Plattform (Zero Trust Network Access) und bietet:
- Leistungsstarke Alternative zu VPN: Ersetzen Sie riskante, überlastete VPNs durch ZPA, um unnötiges Traffic-Backhauling zu vermeiden und einen sicheren, latenzarmen Zugriff auf private Anwendungen zu erhalten.
- Sicherheit für hybride Belegschaften: Stellen Sie Ihren Usern sicheren standort- und geräteunabhängigen Zugriff auf Webanwendungen und Cloud-Services mit optimaler User Experience bereit.
- Agentenloser Zugriff für externe User: Weiten Sie den sicheren Zugriff auf private Anwendungen auf u. a. Anbieter, Auftragnehmer oder Lieferanten aus und unterstützen Sie nicht verwaltete Geräte ohne Endgeräte-Agent.
- IIoT- und OT-Konnektivität: Durch schnellen, zuverlässigen und sicheren Remotezugriff auf IIoT- und OT-Geräte werden Wartungsaufgaben und Fehlerbehebung vereinfacht.


