In a matter of years, we’ve seen Black Friday and Cyber Monday become two of the most anticipated days of the calendar year. While consumers eagerly await the chance to buy this season’s hottest gifts, what they don’t realize is that hackers are also anticipating a holiday treat: their personal data. This weekend, Zscaler uncovered a campaign where malware turning the holiday shopping season into an opportunity to scam large number of people by creating fake apps offering early access to Amazon.com Black Friday and Cyber Monday offers and deals.
The Zscaler research team recently came across one such fake amazon app which was masked as an Amazon.com Black Friday deals app, but actually intended to collect victim's personal data. The URL from where this fake app is downloaded is as shown below:
- URL : http[:]//amazon[.]de[.]offer47263[.]cc/amazon[.]apk
From the URL it can be observed that the malware authors are using cyber squatting to fool the victim and portraying itself as a legitimate Amazon site.
Once the application gets installed it disguises itself as a legit Amazon app.
 |
| Icon |
When the user starts this installed fake Amazon app, it loads another app named "com.android.engine" as seen below.
 |
| Loading application dynamically |
This newly loaded child application asks for administrative privileges and other risky permissions like sending SMS and dialing phone numbers.
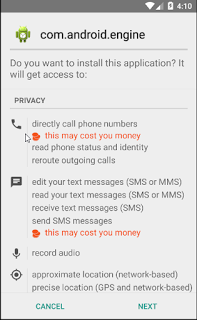 |
| Permissions |
This newly loaded app will first register itself as a service. Even if we remove the fake Amazon app, the "com.android.engine" app will stay persistent and keep doing its activity in the background. Once this malicious app is installed on the victim's phone, the fake Amazon application will start giving the error message: "Device not supported with App". This forces the victim to delete the fake amazon app thinking that there were some errors while installing it. As the malicious child app does not have any icon, it is quite difficult for the common users to remove the app.
The presence of this app can be seen in Settings>Apps>Running Applications section of device as shown below.
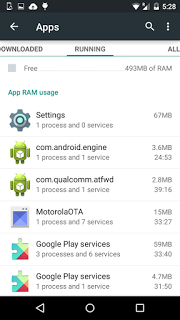 |
| Silently working in backgroud |
 |
| Administrative access |
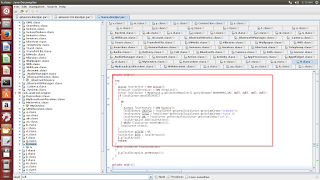
This loaded malicious application has code for harvesting user's personal data.
The following code routine present in the app is used to collect victim's browser history and bookmarks.
 |
| Browser data |
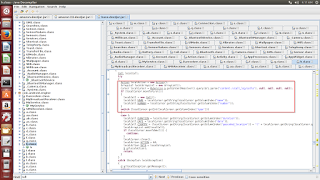
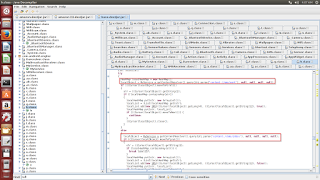
It is also able to harvest the call logs, received inbox messages and segregate it into sender's numbers, SMS body, received incoming call number and contact name etc as shown below.
 |
| Call logs |
 |
| Inbox messages |
The malicious app also gathers victims contact details.
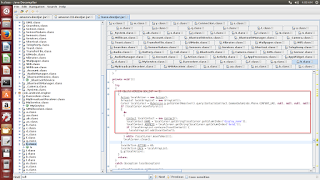 |
| Contacts |
This particular piece of malware was also found to be communicating with an IP address in Canada, "198[.]50[.]169[.]251" on port 4467 probably sending the harvest data through network socket.
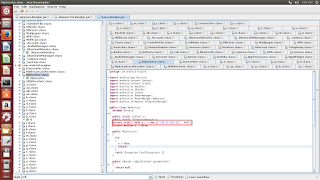 |
| Hard coded IP |
The following packet capture shows the malware communication with its C&C(Command and Control Center).
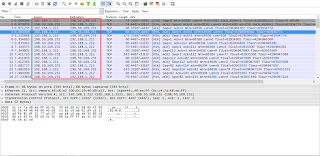 |
| Packet Capture |
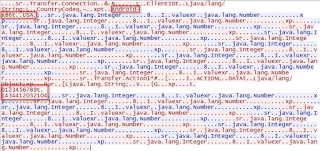 |
| Data being sent |
Especially during this holiday season, consumers need to be aware of the applications they’re downloading and stay away from such fake apps. Always install applications from legitimate app stores and websites. Be aware of the permissions asked by the application during installation. Shopping apps should not be asking for access to your contacts or SMS. Keeping an eye on the permissions used by the app can save you from installing such fake apps.
Happy Thanksgiving to all !!

















