Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Independence Day greeting campaign delivers Emotet
Recently, Zscaler's research team, ThreatLabZ, came across malicious Microsoft Office documents delivering Emotet malware via attachments using "Greeting Card" as the document name. The malware author leveraged the popular 4th of July holiday, the USA's Independence Day, to lure users into downloading and opening the malicious documents. We saw over two dozen unique payloads hitting our Cloud Sandbox in the 48-hour span from July 2nd to July 4th earlier this week. The filenames and hashes for these attachments are shown below:
|
Dateiname |
Hashes |
|
Greeting-Card-07-04-2018.doc |
88b9cff1d3c253f93c56c1a3a3c78800 |
|
Greeting-Card-July-4.doc |
3fe87f1b847a8a10989342fb9a92e7c9 |
|
Greeting-Card.doc |
223c733af5b6036d855c7c9177116ef4 |
|
Greeting-Card-July-4.doc |
229e78f0da36f6ad099d6fc35f154a5d |
|
Greeting-Card-07-04-2018.doc |
6c0c7ee1f783a1465d1fcad1b227aa43 |
|
Greeting-Card-07042018.doc |
57fc905430afb5323c68e14f28e02f4c |
|
Greeting-Card-07042018.doc |
12e13776e95851ebf61e57e0600dfb4f |
Fig.1: Filenames of the attachments with the hashes
In attempting to open the attachment, the user sees the following social-engineered message asking the user to enable content, which will execute the malicious macro in the background. Microsoft Office by default disables automatic execution of embedded macros until the user specifically selects "enable content."
Fig. 2: Fake Office message that asks user to enable macros
Macro obfuscation and de-obfuscation
There is only one macro in the document named Sub_Autoopen(). It includes a lot of junk code to throw off security researchers attempting to analyze it.
Fig. 3: Embedded obfuscated macro triggering with AutoOpen
The code links the values stored in the variable and then runs the whole command with wscript.exe.
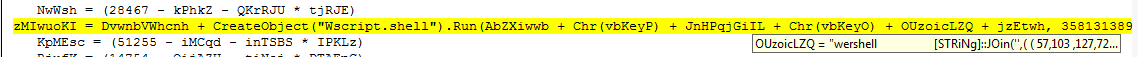
Fig. 4: PowerShell command being de-obfuscated and executed
In the above snapshot, the code is executing Wscript to download a payload using the PowerShell script. The parameters are stored in “OUzoicLZQ.” The PowerShell script is highly obfuscated making it harder to analyze.
Obfuscation script:
Fig. 5: Obfuscated PowerShell command
In the script, we can see it is using: (GV '*Mdr*').nAmE[3,11,2]-jOIN''). This is basically for “iex,” which stands for invoke expression. The Invoke-Expression cmdlet ("command-let") evaluates or runs a specified string as a command and returns the results of the expression or command. Using the for loop, it is taking characters from an array one by one as a string and XORing with “1d,” and, finally, making the full string the full command string using the JOIN method.
De-obfuscation of PowerShell parameters:
Fig. 6: De-obfuscated PowerShell command parameters
The code then connects the user's machine to a remote server, where it will download the Emotet payload, dropping to the temp directory in Windows:
‘C:\Users\user\AppData\Local\Temp\
Emotet payload
Emotet creates a copy of itself in “C:\windows\system32\” with the filename created by appending two strings from a predetermined set of hard-coded strings. The combination of strings is chosen based on “volume serial number” of the infected system’s volume.
Creates Mutex : PEM
For a detailed technical analysis of the Emotet payload, please check our previous blog here.
Zscaler Cloud Sandbox report for one of the greeting card payloads is shown below:
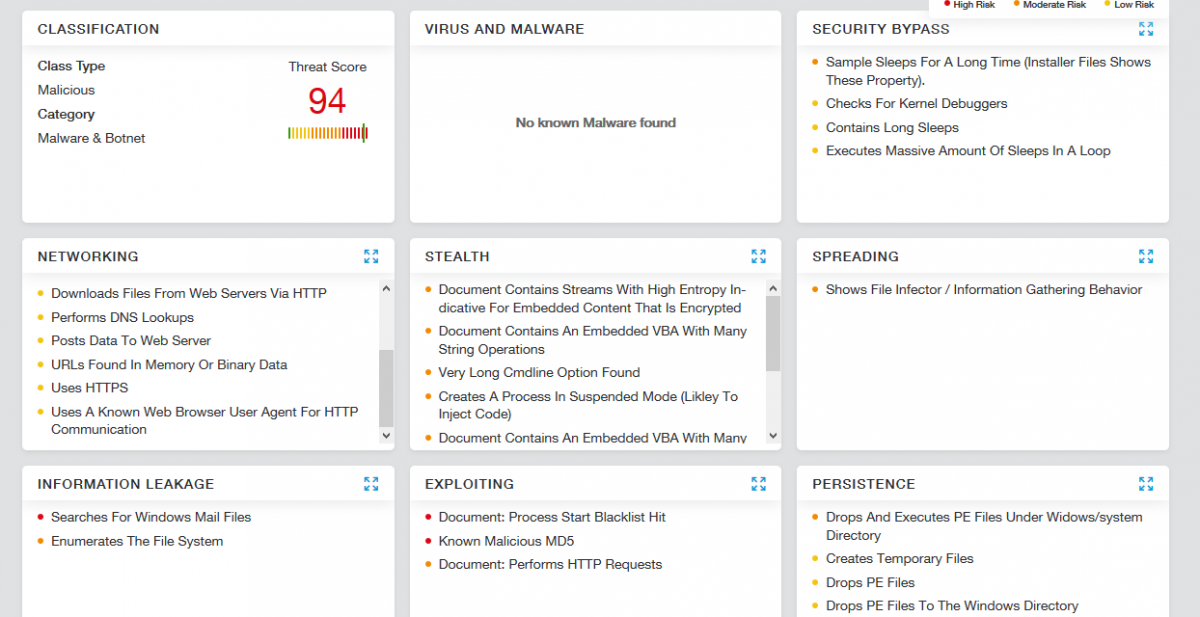
Fig. 7: Zscaler Cloud Sandbox report
Kompromittierungsindikatoren
Download attachment URLs:
www.dokassessoria[.]com.br/independence-day/
www.xiaoguoyx[.]com/4th-july/
pds[.]org.pl/independence-day-greetings/
www.acqi[.]cl/independence-day-greetings/
Malicious document MD5s:
88b9cff1d3c253f93c56c1a3a3c78800
3fe87f1b847a8a10989342fb9a92e7c9
223c733af5b6036d855c7c9177116ef4
229e78f0da36f6ad099d6fc35f154a5d
6c0c7ee1f783a1465d1fcad1b227aa43
57fc905430afb5323c68e14f28e02f4c
12e13776e95851ebf61e57e0600dfb4f
Emotet domain:
dessertcake[.]com.ua/he4f
ky663[.]com/zzd
hunter-kings[.]com/wp-content/czVbGb
dotlenieni[.]pl/Fk5j
clubvolvoitalia[.]it/r3z6
ecuadoresort[.]com/Oa
beraysenbas[.]com/hs2Jv5Y
Emotet executable MD5s:
27e90f2bc9a214b36a59e4ca0b18e75e
D620a9a598f8848c05f72b025f01289b
Ed0abac215c27665005271cfbf77c027
9295c23c16cb8615e4349830df30cc12
c0ebf36bb0f204bd76cb33e7d6e50678
Emotet C&C
92.27.116.104
24.173.127.246
24.121.176.48
186.71.61.90
45.73.1.90
24.234.175.215
24.119.116.230
121.50.43.110
149.62.173.247
12.182.146.226
24.229.49.37
68.2.97.91
216.21.168.27
46.105.131.69
99.224.5.162
69.17.170.58
199.119.78.9
24.74.74.183
157.7.164.23
178.21.113.145
187.178.17.209
118.244.214.210
187.156.24.43
108.170.54.171
177.99.167.185
203.201.60.206
72.0.255.155
194.88.246.242
80.153.201.243
27.50.89.209
206.210.104.194
222.214.218.192
76.72.225.30
203.45.184.52
70.182.77.184
71.244.60.231
146.185.170.222
46.105.131.87
193.251.43.125
78.47.182.42
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.











