Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Empfehlungen zum Schutz: Angriff auf die 3CX-Lieferkette
Update [31.03.2023 17:00 Uhr PST]: Wir haben einen Blog-Artikel veröffentlicht, in dem wir den Angriff auf die 3CX-Lieferkette detailliert analysieren.
Hintergrund
Am 30. März 2023 veröffentlichte 3CX eine Sicherheitswarnung für die mit Update 7 bereitgestellte 3CX Electron Windows App, in der User über einen Lieferkettenangriff informiert wurden. Das Problem betraf ausführbare Dateien sowohl unter Windows als auch unter MacOS.
Welches Risiko besteht konkret?
Die betroffene 3CX Electron Desktop App wurde zusammen mit einer infizierten Bibliotheksdatei namens ffmpeg.dll bereitgestellt. Diese infizierte Bibliothek lädt eine weitere verschlüsselte Datei namens d3dcompiler_47.dll herunter, über die auf .ico-Dateien zugegriffen werden kann, die auf GitHub gehostet werden und CnC-Informationen enthalten. Diese CnC-Domains werden wiederum verwendet, um die endgültige Payload zu übertragen, mit der der Angreifer schädliche Vorgänge in der Umgebung des Opfers durchführen kann. Im folgenden Diagramm sehen Sie die Abfolge der Angriffsphasen.
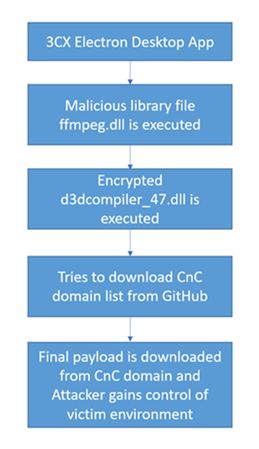
Bei unseren Untersuchungen haben wir festgestellt, dass die Angriffe seit Februar stattfinden. Wir werden in Kürze detailliertere Analyseberichte veröffentlichen.
Welche Systeme sind betroffen?
Sowohl die Windows- als auch die Mac-Versionen der 3CX Electron Windows App sind betroffen.
- 3CX Electron Windows App Version 18.12.407
- 3CX Electron Windows App Version 18.12.416
- 3CX Electron Mac App Version 18.11.1213
- 3CX Electron Mac App Version 18.12.402
- 3CX Electron Mac App Version 18.12.407
- 3CX Electron Mac App Version 18.12.416
Wie können Sie Ihre Organisation schützen?
- Wenn in Ihrem Netzwerk Systeme mit diesen kompromittierten Versionen der 3CX Electron Desktop App auftauchen, deinstallieren Sie die Software bitte.
- Ermitteln Sie die infizierten Systeme, indem Sie die Client-Details in Ihren SIEM-Logs auf Systeme überprüfen, die versuchen, eine Verbindung zu den im Abschnitt „Kompromittierungsindikatoren“ dieser Meldung genannten Indikatoren herzustellen.
- Die Kommunikation mit CnC-Domains kann reputationsbasiert blockiert werden, doch die CnC-Kommunikation verwendet das HTTPS-Protokoll. Aktivieren Sie daher die SSL-Überprüfung, damit die von solchen schädlichen Domains heruntergeladenen Inhalte gescannt werden können.
Schutzmaßnahmen von Zscaler
Erweiterte Cloud Sandbox
- Win32.Trojan.3CX
Advanced Threat Protection
- Win32.Trojan.3CX
- HTML.MalURL.Gen.XO
Kompromittierungsindikatoren
CnC-Domains:
- raw[.]githubusercontent[.]com/IconStorages/images/main/
- visualstudiofactory[.]com
- sourceslabs[.]com
- sbmsa[.]wiki
- qwepoi123098[.]com
- journalide[.]org
- dunamistrd[.]com
- azureonlinestorage[.]com
- azureonlinecloud[.]com
- akamaicontainer[.]com
- zacharryblogs[.]com
- Soyoungjun[.]com
- pbxsources[.]com
- pbxphonenetwork[.]com
- pbxcloudeservices[.]com
- officestoragebox[.]com
- officeaddons[.]com
- msstorageboxes[.]com
- msstorageazure[.]com
- msedgepackageinfo[.]com
- glcloudservice[.]com
- azuredeploystore[.]com
- akamaitechcloudservices[.]com
Schädlicher Hash
- d5101c3b86d973a848ab7ed79cd11e5a
- ca5a66380563ca4c545f1676c23bd95d
- 6426fe4dc604c7f1784ed1d48ab4ffc8
- 82187ad3f0c6c225e2fba0c867280cc9
- 74bc2d0b6680faa1a5a76b27e5479cbc
- f3d4144860ca10ba60f7ef4d176cc736
- bb915073385dd16a846dfa318afa3c19
- 9833a4779b69b38e3e51f04e395674c6
- 0eeb1c0133eb4d571178b2d9d14ce3e9
Ausführlichere Informationen zu den von Zscaler veröffentlichten Bedrohungssignaturen finden Sie in der Zscaler Threat Library.
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.




