 A detailed analysis was provided, here, on the new version of the Storm Worm making it's rounds this week. I went looking in our logs for HTTP POSTs to three and four character GIF and JPG files with relatively small request and response sizes (
A detailed analysis was provided, here, on the new version of the Storm Worm making it's rounds this week. I went looking in our logs for HTTP POSTs to three and four character GIF and JPG files with relatively small request and response sizes (
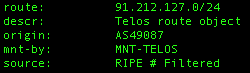
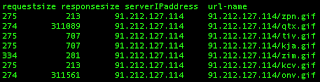
A small snippet of transactions:
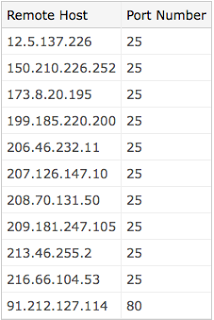
There is a ThreatExpert report on the related server / malware, which is identified as Email-Worm.Zhelatin (name used by Kaspersky and F-Secure for the Storm Worm). The infected hosts connect out to mail servers in attempts to mass-mail and infect others. Here is a list of some of the email servers that it connects to:
Keep an eye out for these types of transactions within your networks.
Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Storm Worm 2.0
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.




