Last week, 64 of the best men's college basketball teams (68 if you count the First Four games) began their quest to cut down the nets in Minneapolis on April 8. Since the opening day of the NCAA men's college basketball tournament isn’t a national holiday, most fans were likely at work when the tournament tipped off. But, that shouldn’t stop them from seeing their alma mater try to upset a national powerhouse or watching a No. 12 seed knock off a No. 5 seed. Thankfully, fans can stream the whole tournament through the CBS Sports website.
ZscalerTM ThreatLabZ noticed increased activity on sports and media sites during the games on the Zscaler cloud platform. However, IT managers or productivity hounds need not panic and pull the curtain on this viewing activity. There are very good reasons to consider allowing your diligent and fanatic workers a chance to cheer for their team (or just to earn some side hustle on the office bracket challenge pool). The most important reason being that blocking official streams sends users elsewhere to watch unofficial streams. These unofficial streams can lead to very real security incidents if left unchecked.
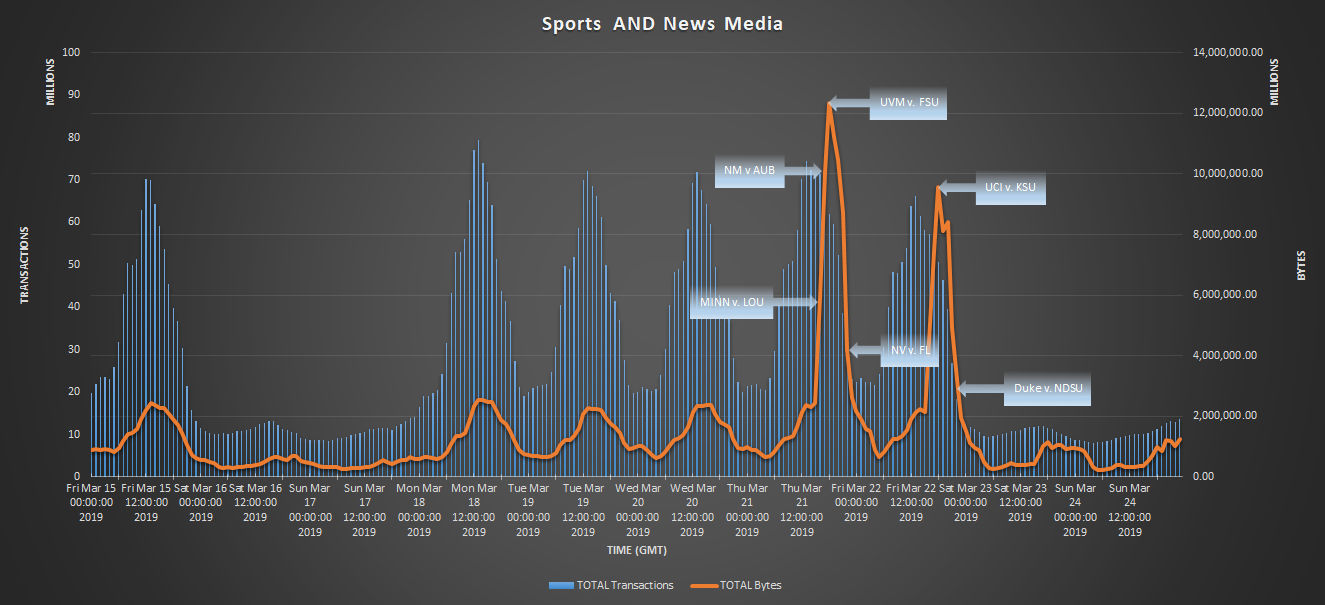
Figure 1: Sports streaming media during NCAA Tournament for the past 10 days.
Figure 1 shows just a portion of the traffic observed by the Zscaler Cloud that is generated by streaming services during the tournament. A steady flow can be seen as far as transaction count goes, but the highlight is the total volume of bytes, which peaks at 12.35 TB/per hour at one point. There is so much interest in the first round of the NCAA tournament that it is better to just allow streaming from legitimate sites if your internal infrastructure can support the load. Figure 2 shows the top official streaming sites that were visited across the Zscaler cloud in past week for NCAA games. Blocking this activity might lead a portion of the viewership looking for alternative sites with less-respectable online reputations.
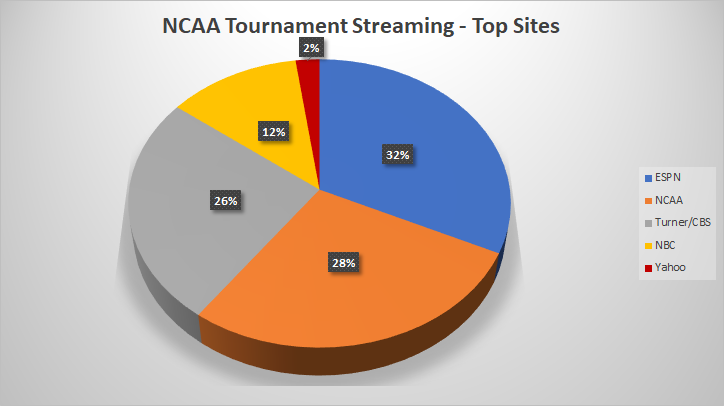 Figure 2: Top sites accessed for NCAA Tournament streaming.
Figure 2: Top sites accessed for NCAA Tournament streaming.
To see just how bad it can get out there, the ThreatLabZ team did an analysis of some attacks seen while searching for unofficial NCAA streams. What we found was a series of adware installers, phishing attacks and fraudulent security warnings leading to malicious browser plugins.
Searching for "ncaa live stream free" in Google resulted in multiple phishing links in the top 50 results.
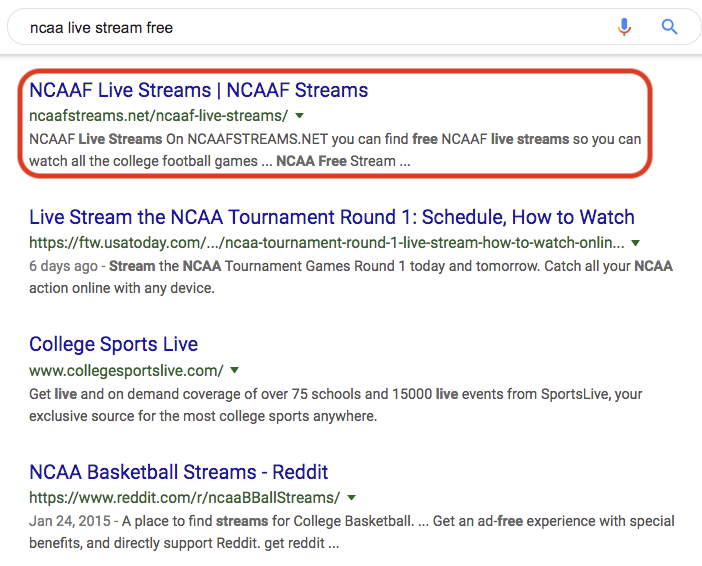
Figure 3: An adware/phishing link in the top 50 Google search results.
Adware/phishing scams
One of the malicious streaming sites that we came across, streamcartel[.]org, is laced with adware on almost each of its pages. When the visitor clicks anywhere on the page or attempts to close the ad, a new tab opens up, prompting the user to install of a fake browser extension.
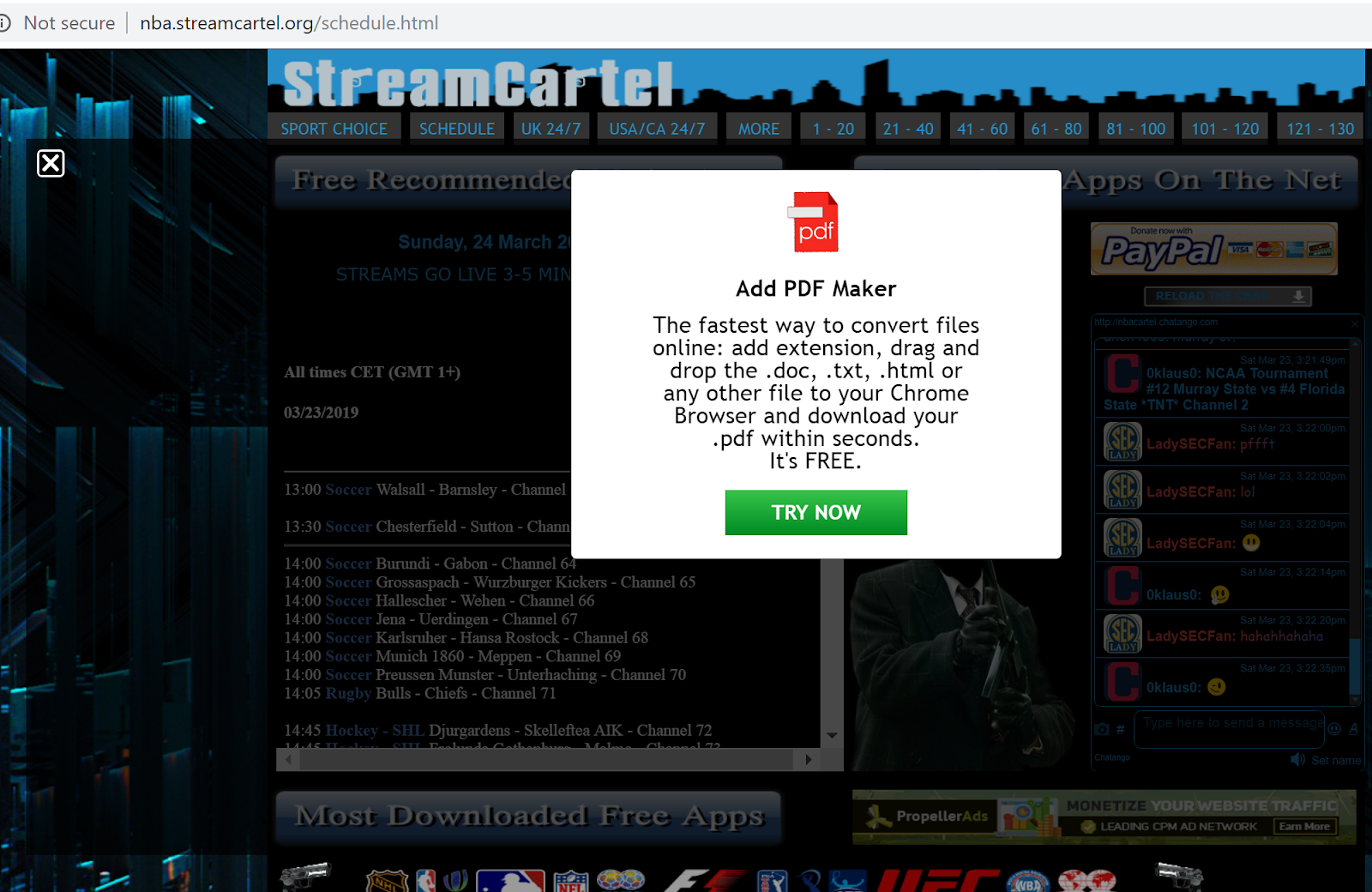
Figure 4: Streamcartel[.]org's NBA schedule page displaying a fake plugin ad.
According to information from Whois, sawlive[.]tv was registered one year ago during the NCAA tournament. It also uses other sporting events for enticing users to visit the site. One of the malicious ads from the site redirects to a Windows fake security warning page.
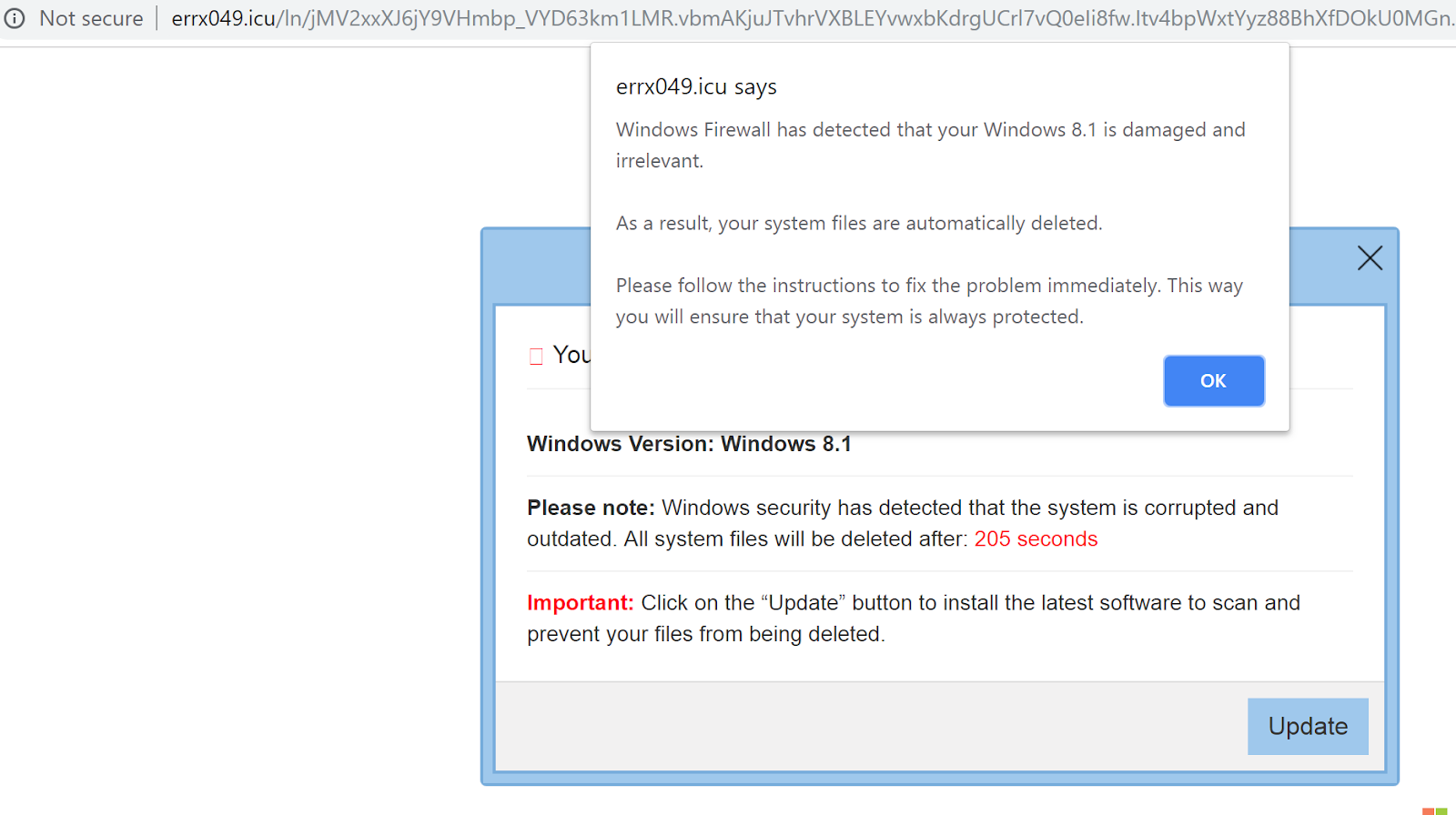
Figure 5: Fake security warning ad/page from Microsoft Windows Firewall.
The goal of this adware site or of any other is to make money by delivering unwanted ads to the user. In addition to that, this site also has a PayPal donation link asking visitors to donate money.
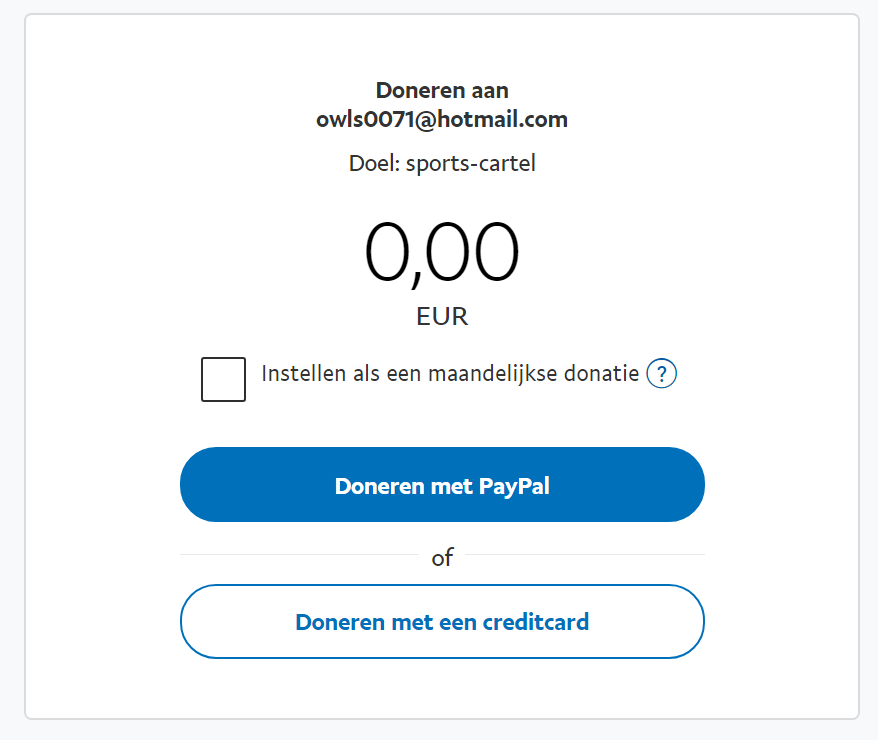
Figure 6: PayPal donation page for owls0071@hotmail.com (in Dutch).
Behind the scenes
The site is embedded with player/content from sawlive[.]tv, which delivers more adware. These sites serve JavaScript obfuscated using JSF*ck, an encoding mechanism that uses only six characters to express any character. Here, 5,518 characters were sent as part of a response and, when deobfuscated, resulted into only 10 characters (“sawlive[.]tv”).

Figure 7: JavaScript obfuscated using JSF*ck, served by sawlive[.]tv.
This obfuscated JavaScript redirects to a request where the malicious server responds with more obfuscated JavaScript.

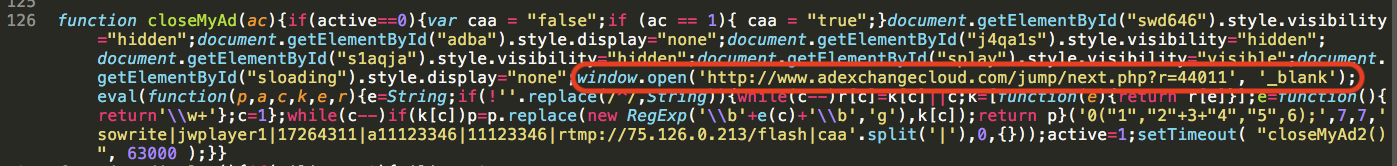
Figure 8: Another cycle of obfuscated JavaScript served by the malicious site.
Whenever the user attempts to click or close the ad, a new browser tab is opened with a request to http[:]//www[.]adexchangecloud[.]com/jump/next[.]php?r=44011, which prompts the user to install a fake browser plugin or scareware alerts or additional adware. One of the ads redirects to fake “Adobe Flash Player” update as shown below:
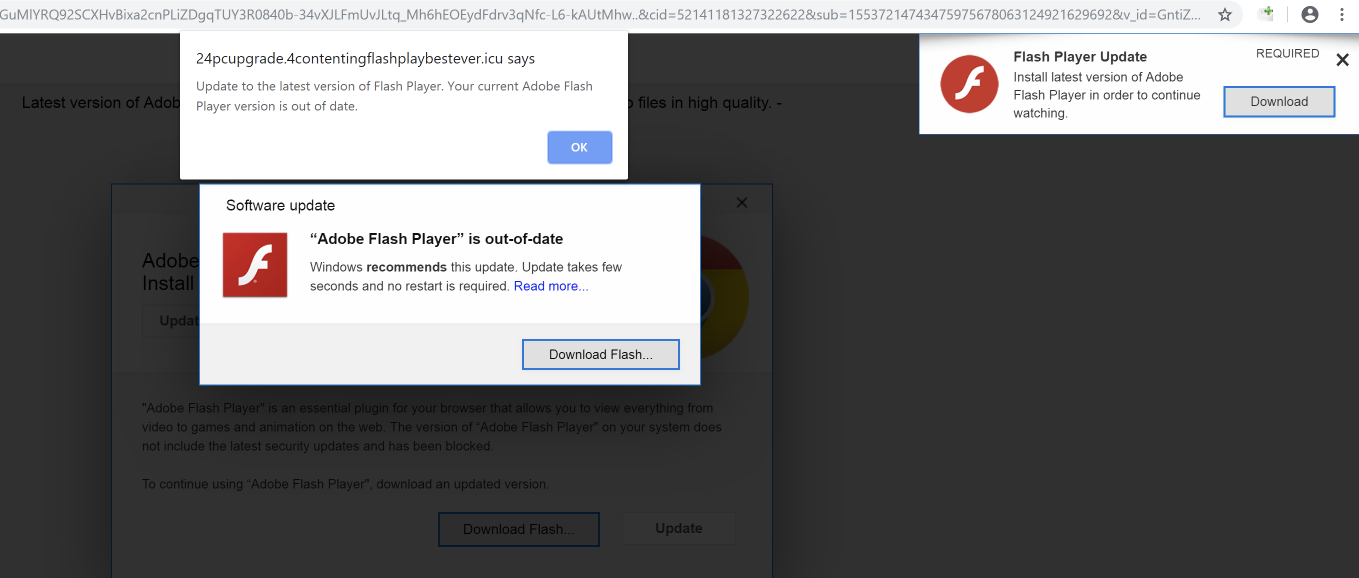
Figure 8: Fake “Adobe Flash Player” update ad.
The download/installer is flagged as malicious by our Zscaler Cloud Sandbox and also by VirusTotal.
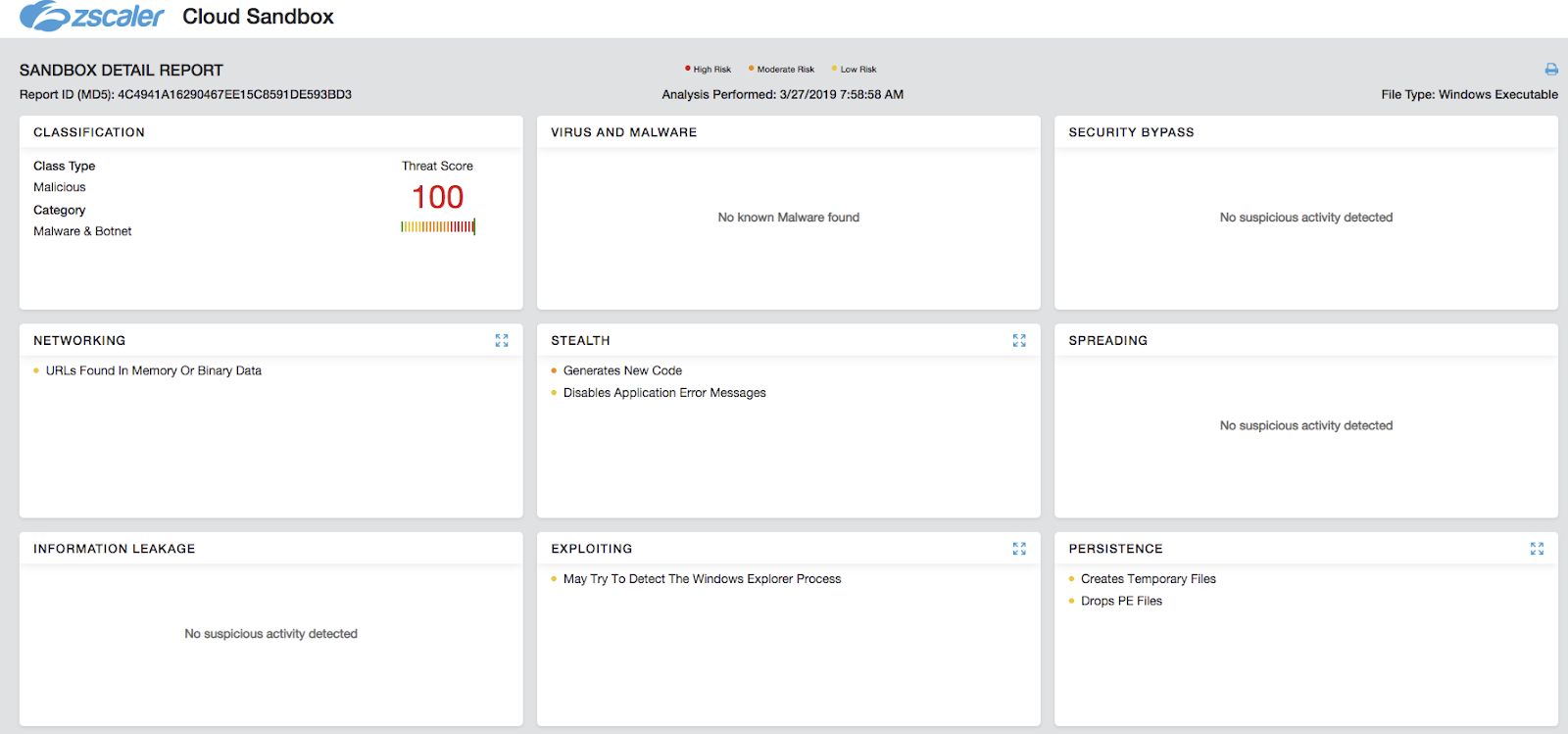
Figure 9: Zscaler Cloud Sandbox report for “Fake Flash Player”.
Typo-squatted domains
As part of every phishing/scam campaign that abuses current trends/keywords, there are typo-squatted domains for terms associated with the NCAA tournament. Here are a few domains that have been registered in the past 10 days:
marchmadnessresults[.]com
watchmarchmadnesslive[.]com
betmarchmadness[.]fan
marchmadness[.]mba
marchmadness[.]rocks
Conclusion
The NCAA tournament is a massive draw for users around the nation. Taking a measured approach to how it is handled is critical for all businesses. The examples laid out should highlight the diversity of threats that attempt to exploit the excitement around the NCAA tournament. We encourage readers to exercise caution when doing searches or clicking on links related to streaming the tournament. Zscaler ThreatLabZ continuously monitors online activity worldwide to ensure that Zscaler customers are protected from threats, even if they become tricked into clicking a nefarious link.
IoCs
adexchangecloud[.]com
adexchangemachine[.]com
go[.]onclasrv[.]com
gsafe[.]getawesome1[.]com
inter1ads[.]com
onclickmega[.]com
sawlive[.]tv
tgun[.]tv
urldelivery[.]com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Chris Mannon and Krishna Kona are Sr. Security Researchers at Zscaler.





