Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Wie Erdnussbutter und Schokolade: So gut harmonieren virtuelle Desktop-Infrastruktur und die Zscaler Zero Trust Exchange
Mit Zscaler Private Access (ZPA) und Zscaler Internet Access (ZIA) bietet Zscaler zwei leistungsstarke Lösungen, die gerade auch in Kombination ein effektives System zur Absicherung von Umgebung mit virtueller Desktop-Infrastruktur (VDI) bilden. Ganz ähnlich wie bei Erdnussbutter und Schokolade also: Wenn zwei großartige Dinge zusammenkommen, kann dabei nur etwas ebenso Großartiges entstehen.
Fraglich bleibt jedoch, wann VDI durch ZPA ersetzt werden sollte und wann die kombinierte Lösung der sinnvollere Ansatz ist. Erdnussbutter und Schokolade mögen eine köstliche Kombination ergeben, aber sie lassen sich nicht einfach gegeneinander austauschen. (Schokoladensirup auf Frühlingsrollen? Vielleicht nicht die beste Idee. Schokoladige Mole-Sauce hingegen …) Das Gleiche gilt auch für die oben stehende Frage: In einigen Fällen kann VDI durchaus gewinnbringend durch ZPA ersetzt werden, aber keinesfalls in allen.
Um solche Fälle voneinander unterscheiden zu können, sollte man sich zunächst einmal bewusst werden, warum VDI überhaupt eingesetzt wird. Ist VDI für die aktuellen Anwendungsfälle tatsächlich noch erforderlich? Wird VDI von allen Usern genutzt oder nur von einer bestimmten Gruppe? Anhand solcher Fragen und Analysen können IT-Verantwortliche sich Schritt für Schritt von den Annahmen lösen, die mit der von herkömmlichen On-Premise- bzw. On-Network-Ansätzen geprägten Denkweise einhergehen.
Typischerweise setzen Organisationen aus einem oder mehreren der folgenden Gründe auf VDI:
- Granularität des Zugriffs: Beschränkung von User-Rechten auf autorisierte Anwendungen
- Einschränkung der Datenresidenz: Gewährleistung, dass Daten a) innerhalb der Unternehmensgrenzen verbleiben und/oder b) niemals auf dem Gerät des Endusers gespeichert werden
- Lokalisierung des Traffics: Minimierung von Latenzen für ressourcenintensive Client-Server-Interaktionen (z. B. Datenbankaufrufe)
- Desktop-Verwaltung oder ‑Optimierung: Bereitstellung eines reibungslosen und lückenlosen Desktop-Erlebnisses für User-Zugriffe von verschiedenen Geräten
- Reduzierung von Software-Lizenzen: Software-Deployment auf einigen ausgewählten virtuellen Desktops statt auf allen User-Geräten
- Unterstützung für Legacy-Anwendungen: Gewährung von Zugriff auf Anwendungen, die ältere Betriebssysteme erfordern
- Traffic-Überprüfung: Nutzung von VDI, um den gesamten Traffic durch lokale Security-Stacks zu leiten
Wenn es Ihnen um den ersten Punkt geht, bietet sich ZPA als VDI-Ersatz an. Mit ZPA profitieren Sie vom Prinzip der minimalen Rechtevergabe und haben die Möglichkeit, autorisierten Usern granulare Zugriffsberechtigungen auf bestimmte Anwendungen zu gewähren. Indem Sie ZPA um Private Service Edge erweitern, können Sie darüber hinaus den Anwendungsfall 2 a) abdecken und dafür sorgen, dass die Kontroll- und Datenebene vollständig innerhalb Ihrer Sicherheitsgrenze für privaten Traffic verbleiben. (In Kürze wird Zscaler mit Cloud Browser Isolation zudem eine weitere ZPA-Integration bieten, um den Anforderungen hinter Anwendungsfall 2 b) gerecht zu werden.) Liegt der Fokus auf einem der anderen Punkte, eignet sich Zscaler als Ergänzung Ihrer bestehenden VDI-Umgebung und der damit einhergehenden beschriebenen Vorteile.
Ganz egal, ob Ihre VDI-Umgebung nun als On-Premise- (z. B. Citrix XenDesktop, VMware Horizon) oder Desktop-as-a-Service-(DaaS-)Modell (z. B. Amazon WorkSpaces, Windows Virtual Desktop) bereitgestellt wird: Mit granularem, Cloud-nativem Zero-Trust-Zugriff bietet Zscaler Ihnen eine zusätzliche Sicherheitsebene für virtuelle Desktop-Lösungen. Hier zeigt sich also, wie aus der Kombination von zwei wertvollen Tools ein noch größerer Mehrwert entsteht: Zscaler ermöglicht dort zentrale Einblicke und Kontrolle, wo User über VDI-Umgebungen auf Ressourcen zugreifen. Die Installation des Zscaler Client Connector auf virtuellen Desktop-Instanzen ermöglicht Einblicke und zentrale Kontrolle hinsichtlich der Ressourcen, auf die User von dort aus zugreifen können.
Verschiedene praktische Kundenbeispiele geben einen Eindruck davon, wie Zscaler Client Connector in DaaS-Umgebungen eingesetzt werden kann, um externen und Software-as-a-Service(SaaS-)-Traffic über Zscaler Internet Access (ZIA) sowie Traffic zu privaten Anwendungen über Zscaler Private Access (ZPA) zu schützen. Eine solche kombinierte Lösung bringt zahlreiche Vorteile mit sich: zentrale Einblicke und Kontrolle, einheitliche Richtlinienkonfiguration für VDI sowie andere Zugriffsarten und eine konsistente Anwendererfahrung – mit der Einschränkung, dass dedizierte VDI-Instanzen für einzelne User vorhanden sein müssen (das entspricht dem, was Amazon „Windows BYOL“ nennt).
Dieser Ansatz erweist sich etwa dort als hilfreich, wo es Mitarbeitern ermöglicht werden soll, von ihren eigenen Geräten aus auf private Anwendungen zuzugreifen, während der Zugang für externe Dritte auf VDI beschränkt bleiben soll. Die zentralen Transparenz- und Kontrollfunktionen, die ZPA bietet, lassen sich auf beide User-Gruppen ausweiten, wie unten in Abbildung 1 dargestellt.
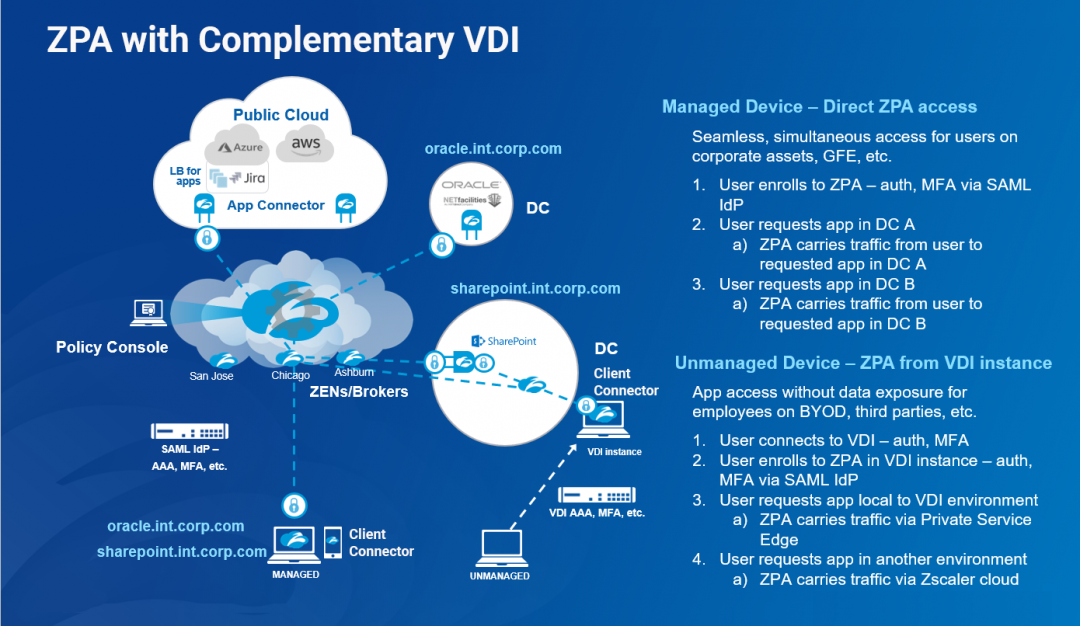
Abb. 1. ZPA als Ergänzung für VDI-Deployments.
Selbst wenn VDI nicht für alle User ersetzt werden muss, stellt sich häufig heraus, dass ZPA die Betreuung zahlreicher User-Gruppen durchaus vereinfachen kann. So haben sich in den Bereichen Finanz- und Versicherungsberatung bereits viele Unternehmen für den Umstieg auf webbasierte Anwendungen (z. B. DocuSign) entschieden. Damit ist VDI für Tausende Anwender womöglich gar keine unbedingte Voraussetzung mehr. Diese Entwicklung macht es erforderlich, Systemarchitekten, Anwendungsverantwortliche und ähnliche Akteure abseits der Netzwerk- und Sicherheitsteams einzubeziehen.
ZPA und VDI: zusammen unschlagbar
Bevor Unternehmen den Schritt gehen, VDI durch ZPA zu ersetzen oder zu erweitern, sollten sie zunächst ein umfassendes Verständnis dafür entwickeln, warum sie VDI nutzen, und abwägen, ob ihre Umgebung dies tatsächlich nach wie vor erfordert. In vielen Fällen macht die Zero Trust Exchange von Zscaler VDI überflüssig, da eine direkte Verbindung mit internen und Cloud-Anwendungen ermöglicht wird – selbst dann, wenn User außerhalb des Perimeters darauf zugreifen.
Um fundierte Entscheidungen treffen zu können, gilt es, die eigenen Annahmen zu hinterfragen und die realen Gegebenheiten umfassend zu analysieren. Wo lohnt sich eher ein vollständiger Ersatz, wo ein Zusammenspiel der Lösungen? Fest steht: Nur wo Komponenten planvoll eingesetzt werden, erfüllen sie am Ende ihren Zweck – darüber lässt sich ebenso wenig streiten wie über Geschmack.
Weitere Ressourcen finden Sie in unserem Wissens-Hub rund um „Work from Anywhere“.
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.





