Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
VPNs sind der neuen Normalität nicht gewachsen
Noch Anfang 2020 hätte ich jeden für verrückt erklärt, der mir weismachen wollte, dass ich demnächst ins Homeoffice umziehen und es monatelang nicht mehr verlassen würde. Anfangs tröstete ich mich noch mit der Hoffnung, dass bestimmt bald wieder alles wieder seinen gewohnten Trott gehen würde. Je länger der Ausnahmezustand jedoch anhielt, desto stärker drängte sich die Frage auf, ob er sich womöglich dauerhaft als neue Normalität verstetigen würde.

Garantiert ging es nicht nur mir so. Viele hielten den schlagartige Anstieg der Remote-Arbeit für einen vorübergehenden Zustand. Sobald die unmittelbare Krise vorbei wäre, so glaubten wir, würde sich die Aufregung um die Hochskalierung der Remote-Kapazitäten – mitsamt den verzweifelten Anrufen bei VPN-Anbietern und Wartezeiten von bis zu drei Monaten für die Lieferung eines einzigen Geräts – wieder legen.
Wer könnte es den IT-Verantwortlichen verdenken, dass sie die Tragweite dieses Wandels nicht sofort begriffen? Vor der COVID-Pandemie beschäftigte nur eine kleine Minderheit der Unternehmen Mitarbeiter, die hauptsächlich oder ausschließlich an Remote-Standorten arbeiteten. Heute befinden sich diese Unternehmen in der Mehrheit.
Entsprechend hat die Umstellung vom Krisenbewältigungsmodus zur nachhaltigen Sicherheitsstrategie bei den Organisationen oberste Priorität. Welche Investitionen sind erforderlich? Ist der Einsatz von VPN weiterhin sinnvoll? Wie sieht es mit Netzwerk-Appliances allgemein aus? Wie gewährleiste ich unter den neuen Vorzeichen zuverlässigen Schutz für Unternehmensdaten?
Fest steht: Der Trend zur Remote- und Hybrid-Arbeit hält auch nach Ende der unmittelbaren Krisensituation weiterhin an. Google und Facebook zählten zu den Vorreitern dieser Entwicklung und kündigten bereits sehr frühzeitig eine Verlängerung der COVID-bedingten Umstellung auf Remote-Arbeit an. Siemens folgte mit einer ähnlichen Ankündigung, die 140.000 Mitarbeiter bis auf Weiteres nicht ins Büro zurückzuholen. Aus IT-Sicht ist zur Unterstützung dieser Trendwende vor allem ein neuer Konnektivitätsansatz erforderlich, der Usern im Homeoffice und an anderen Remote-Standorten sicheren Zugriff auf Unternehmensanwendungen ermöglicht. Mit den Verbindungspfaden müssen auch die Zugriffskontrollen über den klassischen netzwerkbasierten Sicherheitsperimeter hinaus bis zum Standort des Users, zum Gerät und zur Laufzeitumgebung der Anwendung ausgeweitet werden. VPNs, die Verbindungen zwischen einer IP-Adresse und dem öffentlich im Internet exponierten Netzwerk herstellen, bieten hier keine zukunftsfähige Option. Als weitaus effektivere Alternative empfiehlt sich die Bereitstellung einer Zero-Trust-Lösung an der neuen Edge.
Dabei muss die Identität des Users ebenso als entscheidendes Kriterium berücksichtigt werden wie der Sicherheitsstatus des jeweils verwendeten Geräts. Für Organisationen ist die Möglichkeit zur Skalierung der standortunabhängigen Konnektivität eine unverzichtbare Voraussetzung für den weiteren Ausbau ihrer Remote-Belegschaften. Deswegen setzen immer mehr Unternehmen auf einschlägige Lösungen von Anbietern wie Okta, Microsoft, CrowdStrike und eben auch Zscaler. Diese in der Cloud bereitgestellten und engmaschig integrierten Zugriffslösungen eignen sich bestens zum Schutz der neuen Edge – schließlich wurden sie eigens zu diesem Zweck konzipiert und entwickelt.
Remote-Access-VPN hingegen erweist sich als zunehmend untauglich für die Anforderungen dieser neuen Arbeits- und Geschäftswelt. Fast täglich macht eine neue Sicherheitslücke Schlagzeilen. Zu den spektakulärsten zählte die Veröffentlichung von Passwörtern für über 900 von Unternehmen genutzte VPN-Server in einem Hacker-Forum im August 2020. Die Abbildung unten zeigt eine VPN-Passwort-Sicherheitslücke, die auftrat, als ein Angreifer auf der Suche nach einer bestimmten Ressource einen Uniform Resource Identifier (URI) an das VPN-Gateway schickte.
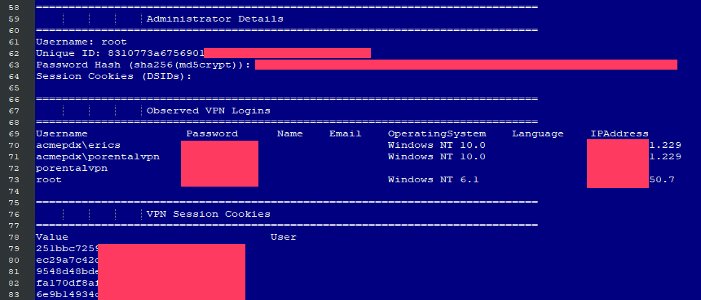
Bildquelle: ZDNet
Ich erhalte immer wieder Anfragen von Kunden, die sich nach den Vorteilen von Zscaler Private Access (ZPA) zum Schutz vor derartigen Angriffen erkundigen. Meine Kollegin Lisa Lorenzin, die vor dem Wechsel zu Zscaler für einen VPN-Anbieter arbeitete, hat dazu Folgendes zu sagen:
- Erstens verfügen die ZPA App Connectors nicht über Ereignisbehandlungsroutinen für eingehende Verbindungen; also können sie von Hackern nicht durch Scannen des Internets entdeckt werden, wie es bei den betroffenen VPN-Servern der Fall war.
- Zweitens werden in unserer Lösung überhaupt keine Anmeldedaten von Usern gespeichert. Zusätzlich bieten wir optional SSO für Administratoren an, sodass es für Hacker unmöglich ist, Anmeldedaten zu stehlen – von Usern sowieso nicht, und von Administratoren im Idealfall ebenfalls nicht.
- Drittens installieren wir regelmäßig Updates für unsere Konnektoren und können dadurch das Risiko ausschließen, dass Hacker eine seit acht Monaten bekannte Sicherheitslücke ausnutzen.
- Viertens wurde dieser Angriff dadurch ermöglicht, dass ein Hacker einen speziell zu diesem Zweck erstellten URI an das VPN-Gateway schickte. Da ZPA App Connectors wie gesagt keine Ereignisbehandlungsroutinen für eingehende Verbindungen haben, sind sie für derartige Angriffe nicht anfällig. Und da ZPA Service Edges nur beidseitig authentifizierte TLS-Verbindungen zulassen, könnte ein Angreifer den URI auch nicht an den Broker senden.
Sogar OT-Netzwerke (Operational Technology) sind mittlerweile nicht vor Angriffen über VPN sicher. Betroffen sind unter anderem systemrelevante Infrastrukturen in der Öl-, Gas-, Wasser- und Stromversorgung.
Nicht zuletzt liegt das daran, dass die IT-Beauftragten vollkommen überlastet sind und kaum die Zeit finden, sich auch noch um VPN-Patches und Updates zu kümmern. Da VPNs den Zugriff auf Netzwerkressourcen ermöglichen, werden sie gerne von Hackern ins Visier genommen, die sich unbefugten Zugriff auf vertrauliche Daten verschaffen wollen. Mit anderen Worten: Die gleichen Tools, die die IT seit 20 Jahren verwendet, um sicheren Zugriff auf Anwendungen zu gewährleisten, stellen nun ein Sicherheitsrisiko dar.
Es gibt jedoch einen Hoffnungsschimmer. Aus Gesprächen mit verschiedenen IT-Beauftragten weiß ich, dass sie gute Erfahrungen mit einem Zero-Trust-Ansatz als Alternative zu VPNs gemacht haben. Robert Berkenpas von Mowi, dem weltweit größten Hersteller von Lachsprodukten, nutzt diesen Ansatz zur Optimierung der Produktivität seiner Mitarbeiter, damit sie einen Beitrag zur Verbesserung der Umwelt- und Nachhaltigkeitsbilanz seiner Branche leisten können. Heute wird sein IT-Team nicht mehr als Kostenstelle wahrgenommen, sondern als Faktor, der sich positiv auf die Geschäftsergebnisse auswirkt. Marc De Serio, CTO der Henry M. Jackson Foundation, nutzt den Zero-Trust-Ansatz, um die Stabilität der Lieferkette zu sichern, die Militärwissenschaftler im Kampf gegen COVID-19 unterstützt . Jay Tillson, Head of Architecture beim Elektronikhersteller TT Electronics, entwickelte eine zukunftsfähige Architektur, die cloud- und identitätsbasierten Zugriff in den Mittelpunkt stellt. (In seiner Live-Session zum Thema erhalten Sie weitere Tipps und Informationen aus der Praxis.)
Ich würde Ihnen empfehlen, sich gründlich mit der Frage auseinanderzusetzen, wie Ihre langfristige Strategie für den sicheren Remote-Zugriff aussehen soll. Welche Erwartungen stellt das Unternehmen an Sie? Welche Technologien sind für eine erfolgreiche Realisierung Ihrer eigenen Ziele sowie der Geschäftsziele der Organisation erforderlich?
Möglicherweise stellen Sie dabei fest, dass Ihr VPN diesen Anforderungen nicht gewachsen ist. Mit dieser Erkenntnis wären Sie keineswegs alleine.
Chris Hines ist als Director of Product Marketing für Zscaler Private Access zuständig.
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.





