Zscaler Blog
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Abonnieren
Datenschutz in der Cloud: Sechs tückische Herausforderungen für Organisationen
Die meisten Menschen denken bei Datenschutzlösungen primär an Data Loss Prevention (DLP). Eine effektive Strategie zum Schutz von Daten in der Cloud erfordert jedoch einen ganzheitlichen Ansatz, in dem DLP nur eine von mehreren unverzichtbaren Komponenten ist. Um einen zuverlässigen Schutz zu gewährleisten, muss DLP auf einem soliden Fundament aus lückenloser Transparenz, robustem Sicherheitsstatus und minimaler Angriffsfläche aufbauen. Bei der Schaffung dieses Fundaments sind sechs entscheidende Herausforderungen zu bewältigen.
Datenschutz in der Cloud: Sechs Herausforderungen für Organisationen
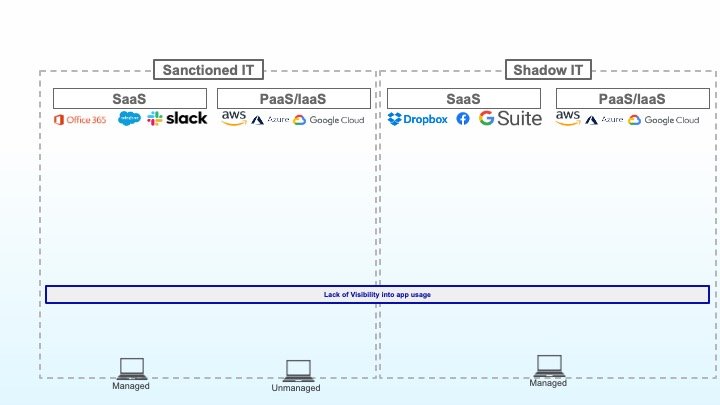
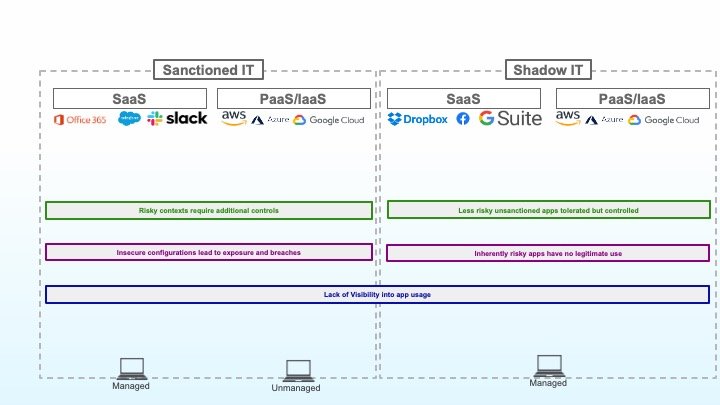
1. Ungenügender Einblick in die Anwendungsnutzung
Lückenloser Schutz setzt lückenlose Transparenz voraus. Entsprechend muss als erste Herausforderung der mangelnde Einblick in die Anwendungsnutzung bewältigt werden. Dies betrifft sowohl Ihre offiziell genehmigten IT-Ressourcen als auch die Shadow-IT.
Im Hinblick auf offiziell genehmigte Anwendungen benötigt die Organisation präzise und zuverlässige Informationen dahingehend, welche Anwendungen zu welchen Zwecken verwendet werden. Je genauer Sie etwa überblicken können, mit welchen AWS-Services Ihr Entwicklungsteam arbeitet oder welche Fremdanbieter-Anwendungen mit Office 365 verbunden sind, desto besser können Sie etwaige Schwachstellen in Ihrer Datenschutzstrategie erkennen.
Im Hinblick auf sogenannte Shadow-IT-Anwendungen, mit denen User ohne offizielle Genehmigung der IT arbeiten, ist Transparenz unbedingt als Entscheidungsgrundlage erforderlich, wenn es darum geht, ihre Nutzung zuzulassen, einzuschränken oder komplett zu verbieten. Dabei ist zu beachten, dass Shadow-IT neben SaaS-Anwendungen zunehmend auch die Nutzung von PaaS/IaaS-Services umfasst. Der Schutz dieser Anwendungen ist mindestens genauso wichtig wie die Kontrolle über inoffiziell genutzte SaaS-Applikationen.
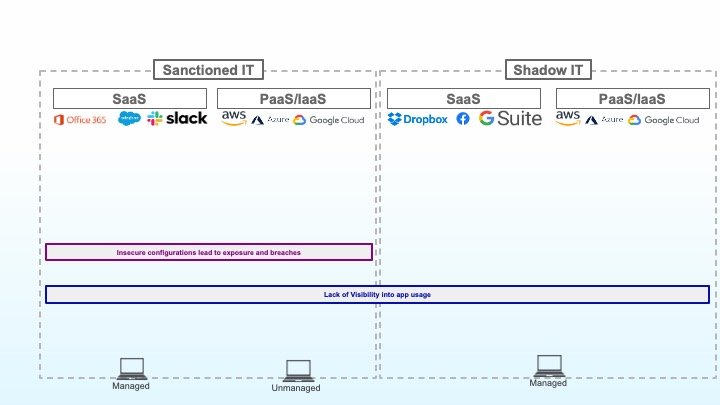
2. Gefährdungen und Sicherheitsverletzungen durch riskante Konfigurationen
Die zweite Herausforderung besteht darin, die Grundkonfiguration der offiziell genehmigten Anwendungen zuverlässig abzusichern. Fehlkonfigurationen in cloudbasierten Speicherlösungen haben im Laufe der letzten Jahre immer wieder zu schlagzeilenträchtigen Datenpannen geführt. Allerdings sind auch andere Cloud-Anwendungen keineswegs vor solchen Fehlkonfigurationen gefeit. Bewältigen lässt sich diese Herausforderung nur durch die präzise Identifizierung und Überprüfung sämtlicher Konfigurationen, die zur Gefährdung vertraulicher Daten führen können, wenn sie nicht ordnungsgemäß abgesichert werden. Dazu zählen Identitätsverwaltung, Verschlüsselung, Netzwerkarchitektur und externe Verbindungen ebenso wie Freigaben zur gemeinsamen Nutzung von Netzwerkbereichen, Laufwerken oder Dateien.
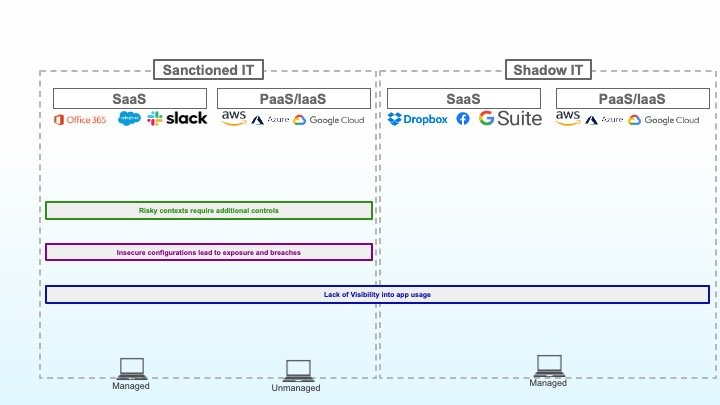
3. Riskante Zugriffsszenarien, für die zusätzliche Kontrollen erforderlich sind
Risikoprofile sind nicht statisch. Neben den entsprechenden Berechtigungen für den Zugriff auf eine bestimmte Anwendung sind weitere Faktoren wie der Standort des Users, der Status des Geräts sowie die Art der angeforderten Inhalte zu berücksichtigen. Wenn ein User an einem unbekannten Standort über ein nicht verwaltetes Gerät vertrauliche Daten herunterladen will, ist das Risiko im Vergleich zu einer Zugriffsanfrage desselben Users über ein verwaltetes und geschütztes Gerät als höher einzustufen. Eine robuste Zugriffskontrolle verhindert Datenverluste, indem gewährleistet wird, dass das jeweils gewährte Zugriffsniveau dem kontextbezogenen Risikoprofil entspricht.
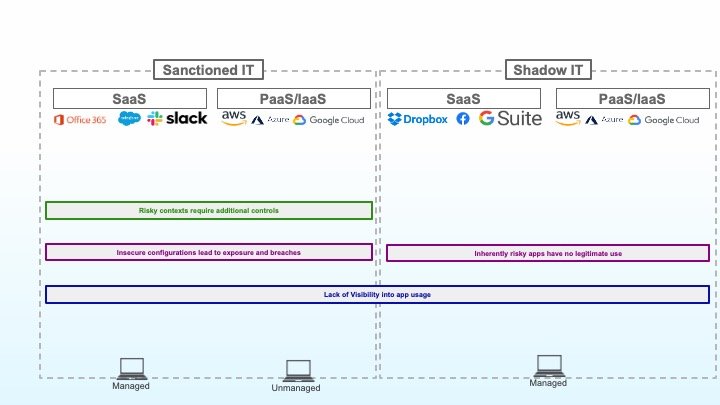
4. Riskante Anwendungen ohne legitimen Geschäftsnutzen
Bei der Analyse von Shadow-IT werden häufig Anwendungen identifiziert, deren Nutzung mit hohem Risiko verbunden ist und keinem legitimen Geschäftszweck dient. Anwendungen, von denen bekannt ist, dass sie Malware hosten, Anwendungen mit fragwürdigen Datenschutzrichtlinien, bisher unbekannte Anwendungen und eine breite Palette ähnlicher unerwünschter Anwendungen sollten in Unternehmensnetzwerken und auf allen verwalteten Geräten vollständig blockiert werden.
5. Kontrollierte Nutzung von Shadow-IT mit geringerem Risiko
Nicht alle inoffiziell genutzten Anwendungen können und müssen blockiert werden. Mitarbeiter nehmen sich heutzutage die Freiheit, ihr verwaltetes Gerät in der Mittagspause auch einmal zu privaten Zwecken zu nutzen: Sie verschicken private E-Mails über das Unternehmensnetzwerk, schauen auf Instagram vorbei oder zahlen Rechnungen – alles Aktivitäten, die für die Organisation mit einem vergleichsweise geringen Risiko von Datenverlusten verbunden sind. Daher wird die Nutzung der betreffenden Anwendungen in der Regel mit bestimmten Einschränkungen zugelassen.
Beispielsweise können Sie entscheiden, dass Ihre User Inhalte auf Social Media zwar anzeigen, aber selber keine Beiträge posten dürfen. Oder Sie können den Mitarbeitern erlauben, E-Mails zu lesen und zu verschicken, aber keine Anhänge hochzuladen. Derartige Zugriffskontrollen können noch vor der Anwendung von DLP-Richtlinien zur Reduzierung des Risikos von Datenverlusten beitragen.
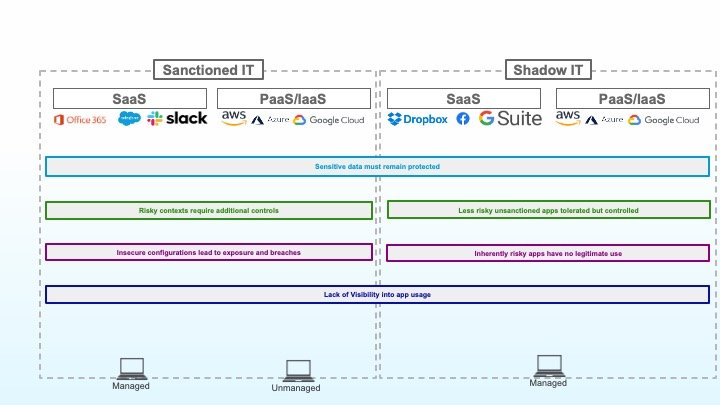
6. Zuverlässiger Schutz für vertrauliche Daten
Als letztes Mosaikstück muss noch ein zuverlässiger Schutz für vertrauliche Daten gewährleistet werden. Inzwischen verfügen Sie über präzise Informationen zur Nutzung von Cloud-Anwendungen und können einen robusten Sicherheitsstatus für diese Anwendungen gewährleisten. Mithilfe von Zugriffskontrollen haben Sie zusätzlich dafür gesorgt, dass riskante Szenarien für den Zugriff auf vertrauliche Daten weitestmöglich blockiert bzw. verhindert werden.
Abschließend müssen nun Inline- und Out-of-band-DLP-Funktionen implementiert werden, die granular kontrollieren, welche User und Anwendungen auf welche Daten zugreifen können.
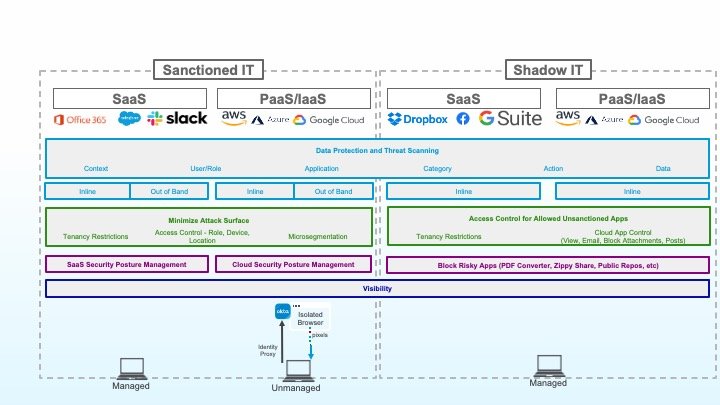
Sechs Herausforderungen, eine überzeugende Lösung
Die Bewältigung all dieser Herausforderungen auf einen Schlag mag schier unmöglich erscheinen. Welche Organisation verfügt schon über die erforderlichen finanziellen Mittel, personellen Ressourcen und freien Kapazitäten, um sechs verschiedene Tools von sechs unterschiedlichen Anbietern anzuschaffen, zu implementieren und fachgerecht zu verwalten?
Mit der Zscaler-Lösung profitieren Sie von einer zentralen Plattform, in der sämtliche erforderlichen Funktionen inbegriffen sind, die Sie zur Bewältigung der beschriebenen Herausforderungen beim Datenschutz in der Cloud benötigen. Unsere ganzheitliche Lösung zum Schutz vor Datenverlusten aus allen offiziell genehmigten Anwendungen und Shadow-IT-Umgebungen basiert auf der Zero Trust Exchange, auf die Tausende Unternehmen weltweit vertrauen. Wenn Sie bereits Zscaler-Kunde sind, nimmt die Konfiguration und Aktivierung dieser Funktionen möglicherweise nur wenige Minuten in Anspruch.
War dieser Beitrag nützlich?
Haftungsausschluss: Dieser Blog-Beitrag wurde von Zscaler ausschließlich zu Informationszwecken erstellt und wird ohne jegliche Garantie für Richtigkeit, Vollständigkeit oder Zuverlässigkeit zur Verfügung gestellt. Zscaler übernimmt keine Verantwortung für etwaige Fehler oder Auslassungen oder für Handlungen, die auf der Grundlage der bereitgestellten Informationen vorgenommen werden. Alle in diesem Blog-Beitrag verlinkten Websites oder Ressourcen Dritter werden nur zu Ihrer Information zur Verfügung gestellt, und Zscaler ist nicht für deren Inhalte oder Datenschutzmaßnahmen verantwortlich. Alle Inhalte können ohne vorherige Ankündigung geändert werden. Mit dem Zugriff auf diesen Blog-Beitrag erklären Sie sich mit diesen Bedingungen einverstanden und nehmen zur Kenntnis, dass es in Ihrer Verantwortung liegt, die Informationen zu überprüfen und in einer Ihren Bedürfnissen angemessenen Weise zu nutzen.
Erhalten Sie die neuesten Zscaler Blog-Updates in Ihrem Posteingang
Mit dem Absenden des Formulars stimmen Sie unserer Datenschutzrichtlinie zu.





