Adopting the public cloud is both a challenge and an opportunity for security professionals. It’s an opportunity because it means a blank slate where mistakes of the past, that you might have been living with for years, can be overcome with a fresh security architecture. At the same time, it is a challenge because the cloud introduces some entirely new security challenges, and changes how you should approach others.
When it comes to the public cloud permissions model, which determines the access paths between users and resources, there are four key differences from traditional data center environments that can have drastic security implications if not addressed properly from the beginning.
Top Four Public Cloud Permissions Challenges
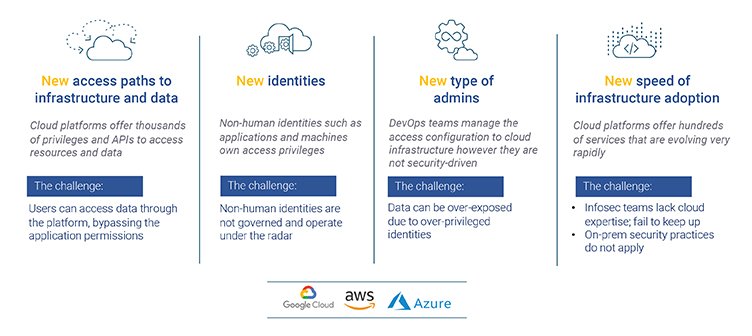
- New access paths to infrastructure and data – Public clouds have a very complicated permissions model, with multiple ways to grant or deny access. A midsize organization, with hundreds of cloud users and tens of thousands of resources, will have tens of millions of individual permissions to manage. There may be several access paths for a user to get access to a resource, with no clear way for an organization to determine who has access to what.
- New identities – In the data center world, you only need to worry about human identities. This is not the case in the public cloud, where human identities are typically outnumbered by non-human identities. These include applications and resources that have their own access privileges, which can be misused and/or compromised. These non-human identities are usually not governed and are often overlooked.
- New type of admins – In the data center, IT and InfoSec typically govern who gets access to what. The cloud world is much more user-driven, with DevOps personnel making access decisions. The challenge is that these folks are motivated by agility and innovation, moving quickly to deliver new products. Security is not job #1, and they frequently aren’t security experts to begin with, leading to excessive permissions assigned to groups of users that don’t need such broad privilege.
- New speed of infrastructure adoption – The major cloud platforms are evolving rapidly, regularly adding new services and features. Microsoft Azure currently lists more than 600 services in its catalog, with AWS and GCP each offering hundreds as well. It can be impossible for InfoSec teams to keep up with such rapid change, a challenge compounded by the fact that these services are frequently available to developers and DevOps as soon as they are announced.
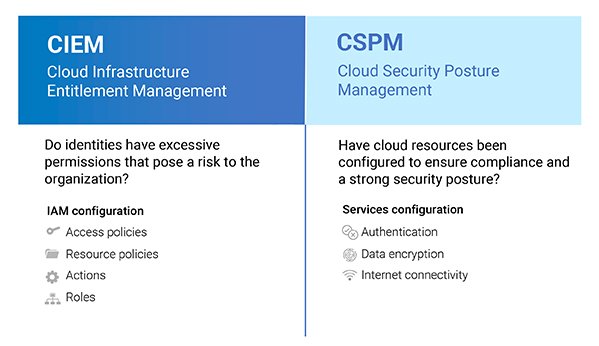
These challenges have all led to the emergence of a new product category: Cloud Infrastructure Entitlement Management (CIEM). A CIEM is a permission security platform designed to mitigate the risk of data breaches in public clouds due to excessive permissions. CIEM products work hand-in-hand with Cloud Security Posture Management (CSPM) tools, which cover the configuration of cloud services. Together, these products comprehensively address security posture risk in the public cloud.
How big is this problem? Gartner predicts that by 2023, IAM misconfigurations will account for a whopping 75 percent of public cloud security incidents. Zscaler CIEM can help accelerate your cloud adoption by reducing risks related to IAM misconfiguration. I’d encourage you to reach out to take a closer look at CIEM and the broader Zscaler Cloud Protection portfolio.
Read more about CIEM:
Blog: Entitlements: The Most Overlooked Risk in the Public Cloud
Blog: CIEM vs. CSPM: Which is Better for Reducing Public Cloud Risk?






