Today, the enterprise looks very different from a decade ago. With users leaving the office to work from anywhere, and more private applications moving to the cloud than ever before, today’s attack surface is the largest it has ever been. Moreover, security threats have become more advanced, especially as applications have left the network.
Unfortunately, in the midst of this evolution, many IT leaders are asked to do more with less. This includes ensuring a healthy security posture in light of a need to reduce costs, transitioning entire infrastructures from legacy technologies to the cloud, all the while needing to remain agile in the face of unforeseen events.
Yes, things are changing. Fortunately, IT has the ability to power this change with a zero trust network access (ZTNA) service. As the internet becomes the new corporate network, ZTNA delivers the security that’s required and the seamless experiences that all users want, while also enabling the business’ success in a cloud-first world.
Let’s take a deeper look into the three main areas that ZTNA can help you power your workforce.

Videos
Deliver the experience users want, finally.
Your workforce comprises remote users, local employees, and third-party contractors, and they are working from everywhere. To ensure they remain productive, they need to be able to access your organization’s private applications at all times. Unfortunately, legacy technology attempts to force users back to a control center located in the data center by backhauling traffic. This introduces latency and slows access speeds for users. Simply put: VPNs are slow, cumbersome, and frankly, outdated.
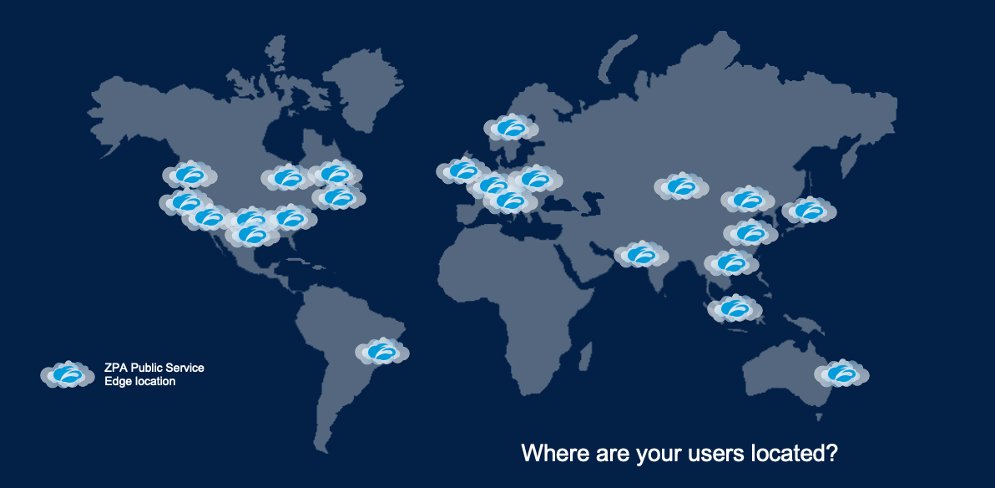
Most ZTNA services are 100 percent cloud-delivered. In the case of Zscaler, we have dozens of brokers across the globe. What this does is bring connectivity closer to the user, resulting in a faster experience. Regardless of where they are accessing from. This also means that access is consistent across all applications, regardless of whether they are legacy apps in the data center or apps running on AWS, Azure, or other public cloud platforms.
Time to get the security you need
Think about the way a lighthouse works. It creates a beacon that ships can use to either guide themselves into port or steer clear of the rocky shore. In either case, the light signals the shore’s location and is viewable to any captain at sea. This is akin to the way network-centric solutions work today. They create a beacon for users (often remote users) to connect to in order to access the network. But that means they are viewable to bad actors, too.
Your network becomes a target for bad actors to deliver internet-based attacks, such as DDoS, ransomware, and countless other forms of malware. Once on the network, users (or malware) can move laterally across it (this is how many malware attacks spread). With each user that connects to your VPN, your attack surface expands—and it only takes one infected device to compromise your entire network.

In light of the vulnerabilities present in this outdated technology, many organizations are implementing a zero trust strategy, with a ZTNA service. ZTNA uses inside-out only connections from the application and from the endpoint, and brokers them together. Apps are never exposed to the internet, and the user is never on the network.
The decoupling of application access from network access is the beauty behind ZTNA. ZTNA only gives authorized users access to individual applications, minimizing risks to your network by preventing any lateral movement. Afterall, users are never on it! Moreover, ZTNA integrates with endpoint solutions, such as CrowdStrike and Carbon Black, to consider device posture when a user requests access to an application. If a device is infected with malware, ZTNA prohibits the device from accessing your team’s private apps.
The business’ success will rely on you.
I know digital transformation is the world’s biggest buzzword, but it really is shaping the current and future needs of your business. The data center is no longer the center of gravity, since private apps are migrating to public clouds and SaaS applications like Salesforce and Office 365 becoming more popular. This move to cloud means more agility for business, which brings with it all kinds of competitive edges.
But they aren’t exactly making it easy for you. IT leaders are being asked to do more with less, which means that it’s key to find ways to optimize budget, reduce risk, and keep the business agile.
Here are the top five challenges IT leaders face:
- Solve the IT skills shortage, allowing the enterprises to make the most of talent on hand
- Deliver a superior user experience for employees and key company stakeholders
- Be adaptive and agile to empower a dynamically changing business
- Reduce the risks that can threaten productivity, IP, and company reputation
- Accelerate the adoption of public cloud and mobile devices
Solving all of these challenges is key to enabling transformation, but none of it would be possible if you rely on a 20-year-old architecture. You must prevent your team from continuing to invest in ineffective, legacy technologies.
If user experience is going to be a priority, you need to focus on fast, local connections without backhauling. If the business needs to be adaptive, you’ll need more cloud-based technologies rather than appliances that add friction to key business projects like M&A. If the business needs to protect sensitive IP, then you need a technology that can protect it from being exposed. If public cloud is important and BYOD is a necessity, then the technology should be built to support them, not repurposed from legacy on-prem, network-centric solutions.
This is why many of the world’s largest organization rely on ZTNA to power their business. These solutions were built to address the specific challenges that IT leaders are facing today.
It’s your time to power it all.
IT now has the chance to rise to the challenge and power the workforce. The first step is making the choice to move beyond the status quo of legacy technology toward propelling the business forward with secure anywhere, anytime private application access.
So, what are you waiting for? Zscaler can help—all you have to do is ask.
Chris Hines is the Director of Product Marketing for Zscaler Private Access






